How Sevco Supports Compliance Frameworks
Meets requirement directly.
Supports requirement or regulatory enablement.
Gap Analysis and Conform Assets
Administrative and Access Checks
Development Assessment
Integrity
Checks
Data Analysis and Inspection
Policies and Procedures
High-level technical review to identify the scope of the audit and align key objectives of the cybersecurity policy, including inventory discovery.
Data gathered to determine how BAUs (business as usual), users, and assets have access to enterprise data and the relationships to it.
Data gathered to prioritize gaps: proactively identifying vulnerabilities, ranking them for remediation, documenting triangulation, and associating supporting data for mitigation.
Assembling proof of findings to ensure cybersecurity policy efficacy and data collected can be used to support risk ranking and report on compliance.
Inspection applied to predetermined data flows to ensure that security controls are in place to protect data in line with the cybersecurity policy.
Checks and balances of the audit: risk assessment, reporting on the distribution and consumption of the security awareness policy, and reporting on overall security posture.
Requirement 2 – “Apply Secure Configurations to All System Components”
Requirements 1, 2, 5, 6, 8, 10, 11, 12
Requirement 2 – “Apply Secure Configurations to All System Components
Requirements 1, 2, 5, 6, 8, 10, 11, 12
Requirements 1, 2, 5, 6, 8, 10, 11, 12
Requirements 1, 2, 5, 6, 8, 10, 11, 12
Requirements 1, 2, 5, 6, 8, 10, 11, 12
Requirement 1.1
Requirement 1.1
Requirement 1.1
CIP 010-3 – Configuration Change Management and Vulnerability Assessments,
CIP-010-2 – Vuln. Assessments
CIP 005-5 – Electronic Security Perimeters, CIP 008-5 – Incident Reporting & Response Planning, CIP-010-2, Configuration Change Mgmt. and Vuln. Assessments
CIP 010-3 – Configuration Change Management and Vulnerability Assessments,
CIP-010-2 – Vuln. Assessments
CIP 005-5 – Electronic Security Perimeters, CIP 008-5 – Incident Reporting & Response Planning, CIP-010-2, Configuration Change Mgmt. and Vuln. Assessments
CIP 005-5 – Electronic Security Perimeters, CIP 008-5 – Incident Reporting & Response Planning, CIP-010-2, Configuration Change Mgmt. and Vuln. Assessments
CIP 005-5 – Electronic Security Perimeters, CIP 008-5 – Incident Reporting & Response Planning, CIP-010-2, Configuration Change Mgmt. and Vuln. Assessments
NIST SP 800-53 Rev. 4 CA-2, CA-7, CA-8, RA-3, RA-5, SA-5, SA-11, SI-2, SI-4, SI-5
NIST SP 800-53 Rev. 4 CA-2, CA-7, CA-8, RA-3, RA-5, SA-5, SA-11, SI-2, SI-4, SI-5
NIST SP 800-53 Rev. 4 CA-2, CA-7, CA-8, RA-3, RA-5, SA-5, SA-11, SI-2, SI-4, SI-5
NIST SP 800-53 Rev. 4 CA-2, CA-7, CA-8, RA-3, RA-5, SA-5, SA-11, SI-2, SI-4, SI-5
NIST SP 800-53 Rev. 4 CA-2, CA-7, CA-8, RA-3, RA-5, SA-5, SA-11, SI-2, SI-4, SI-5
Sections 2, 3, Secure Configuration, Security Update Management
Sections 2, 3, Secure Configuration, Security Update Management
Governance and Risk Management – Risk Assessment
Governance and Risk Management – Risk Assessment
Governance and Risk Management – Risk Assessment
Governance and Risk Management – Risk Assessment
Section 105, 404
Section 105, 404
Section 105, 404
Articles 32 1 (d) Security of Processing 1(d)
Articles 25, 32, 33, 35
Articles 25, 32, 33, 35
Articles 32 1 (d) Security of Processing 1(d)
Articles 25, 32, 33, 35
Articles 32 1 (d) Security of Processing 1(d)
Articles 25, 32, 33, 35
Validate Security Controls Coverage
The recent SEC case against the SolarWinds CISO underlines a shift in compliance: organizations need to prove their security controls are working and enforceable. Having comprehensive visibility and control of asset inventory has been control number one in nearly every security framework and multiple industry compliance mandates, but achieving and proving that control is challenging and often the main bottleneck during a compliance driven security assessment or audit.
Sevco fixes that with a realtime, comprehensive asset inventory that continuously validates and reports on the presence and configuration state of security controls. Sevco provides your team with the evidence it needs to validate the full deployment and efficacy of those controls and ensure compliance requirements are met.
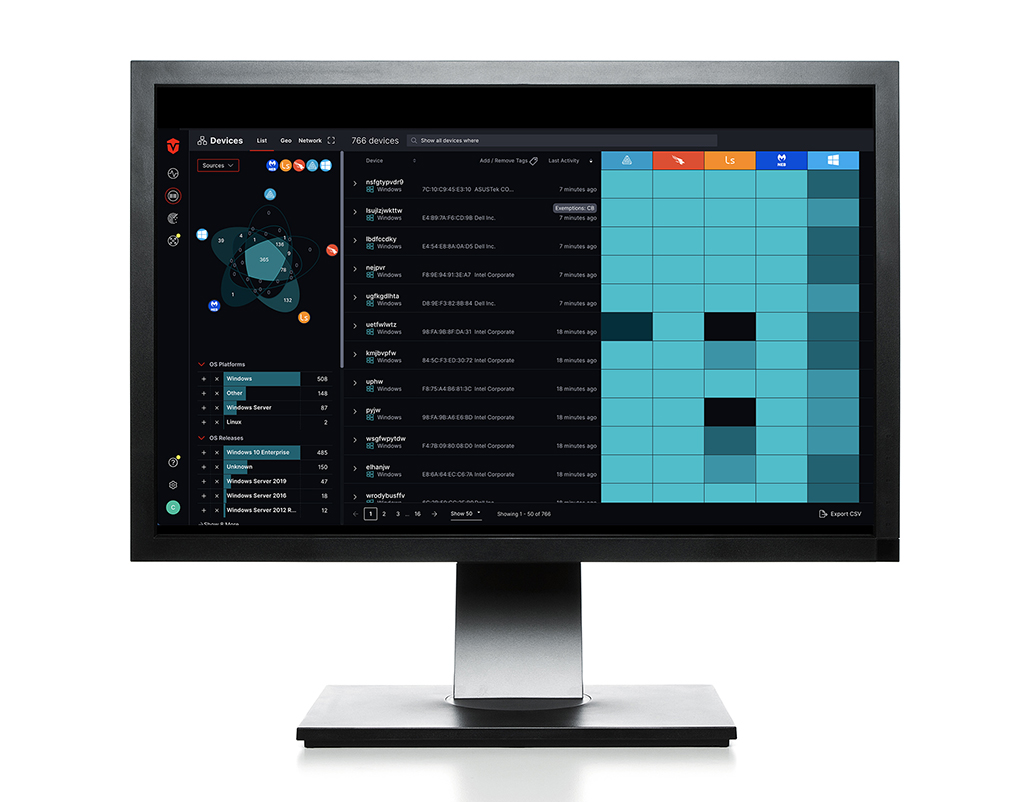
The Sevco platform delivers a comprehensive asset inventory to:
Cut time and resources for audits and assessments
Maintain continuous visibility of your entire asset inventory rather than relying on costly third parties that spend days or weeks pulling data from disparate sources.
Risk rank vulnerabilities
Automate the process of prioritization with full asset telemetry across vulnerabilities including security gaps, exposed assets, and users.
Move from reactive to proactive security
Stay ahead of auditors with automatic alerts, dashboards, and queries to proactively identify missing security controls and vulnerable conditions in real time and before your security audit.
How Sevco drives and validates compliance:
Integrations with leading security tools
Leverage your existing investments and data integrations.
Fully managed and automated asset aggregation, correlation, and deduplication
Delivers the industry’s most accurate security asset inventory backed by automated data associations that address compliance requirements.
Automated alerting
Receive notifications for out-of-compliance devices as soon as they appear.
Outbound integrations to drive, track, and validate remediation
Enable you to quickly address at-risk assets and erroneous security controls.
PCI DSS Compliance.
The PCI DSS framework is a rigorous and time-intensive data security framework. With PCI DSS v4.0 in March 2024, non-compliance and liability include the analysis of data that is both stolen and exposed, making proactive, ongoing assessment of compliance controls with PCI DSS a new necessity. And because organizations often have limited views of their environments, the pre-assessment data gathering phase is often long and requires costly third-parties.
Sevco fixes that by delivering a continuous, comprehensive view of your organization’s environment to quickly identify whether your security posture is up to policy at any point in time, reducing the time spent in the most costly phases of audit and assessment. Sevco automatically uncovers security gaps and EOL assets; proactively uncovers the hygiene, state, and configuration of critical assets; provides the ability to continually risk rank vulnerabilities; and sends alerts when assets fall out of compliance—empowering quick remediation before your audit starts.
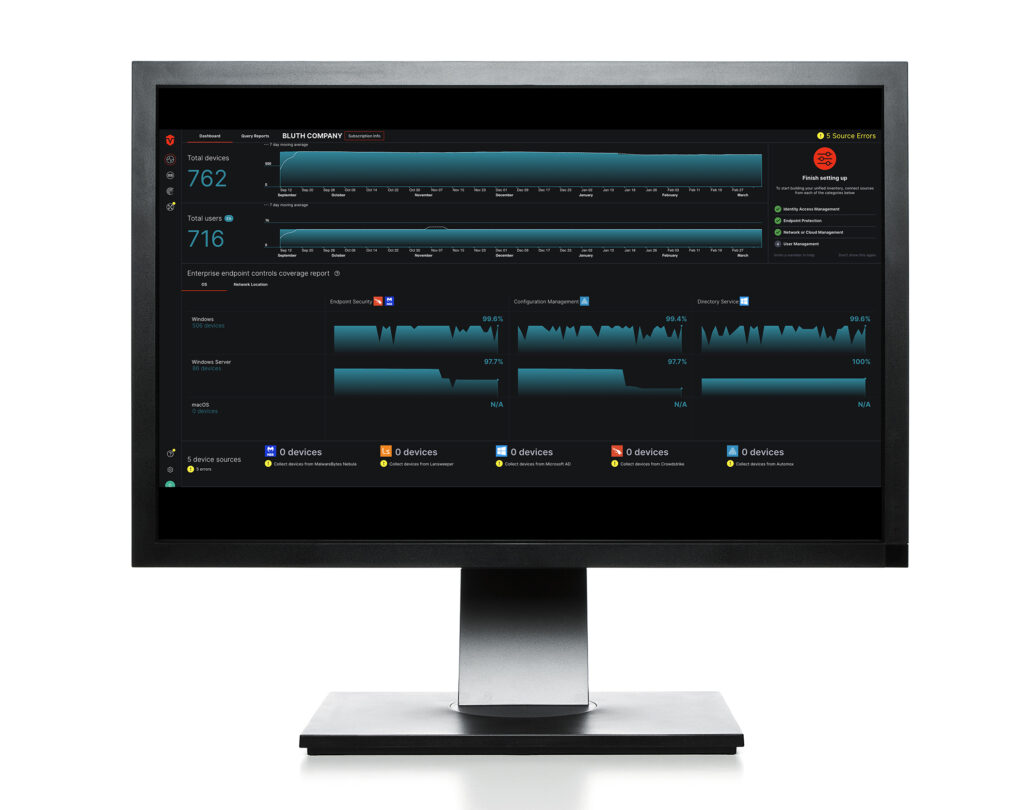
The Sevco platform enables you to:
Analyze and review security controls
With continuous reportable access to network security controls, you can quickly and easily ensure critical assets are protected by security tools.
Risk rank vulnerabilities
Automate the process of prioritization with full telemetry across vulnerabilities including security gaps, exposed assets, and users.
Expedite PCI DSS audits and gap analysis
Cut the time needed for audits and gap analysis from weeks to hours with automated data gathering and scoping.
How Sevco helps meet and support PCI DSS v4.0 requirements:
Fully managed and automated asset aggregation, correlation, and deduplication
Delivers the most up-to-date, comprehensive real-time view of your environment, putting you in complete control of your enterprise assets.
Easy-to-understand interface exposes missing controls coverage and vulnerable conditions
Quickly see exactly which assets to address through Venn diagrams and heatmaps.
Cross-asset queries enable you to search across asset types
Prioritize, tag, and set alerts when an asset falls out of compliance accelerating the risk assessment process.
Find End-of-Life Systems
The cybersecurity landscape is continually evolving. Yet some of the most significant risks aren’t zero-day attacks or sophisticated new supply-chain worms. They are trusted business systems that have been in use for years that have reached the end-of-life (EOL) stage and thus are no longer receiving security updates, introducing unnecessary risk into your IT environment and your security policy.
Sevco fixes that by providing comprehensive visibility into all enterprise assets and whether or not they are protected with security controls, what apps are running on them, and whether those apps are being supported. Sevco can automatically find EOL systems in your environment so you can prioritize and remediate those assets while meeting the compensating controls necessary to remain compliant and secure.
Real-time asset identification
Quickly identify which assets are EOL or end-of-service-life (EOSL) to reduce risk.
Support continuous compliance
Demonstrate and prove compensating controls are in place to protect unsupported EOL assets.
Outbound integrations for remediation
Quickly upgrade, patch, or remove EOL assets.
Explore other use cases.
How the Sevco platform helps people in the trenches every day.
What our customers say about us
"If you have a product that’s not properly checking into a console that you’re paying money to secure, then you have a gap. Not only do we check if the application is running, but all the service is running. Unfortunately, that does not guarantee end-to-end compliance without Sevco. Sevco ensures Greenhill can find and close these gaps before they can be exploited by attackers."
Gabe Cioffi, Greenhill Director of Information Technology
"Sevco’s value cannot be overestimated, just one missed device can compromise an entire company."
Grigiory Milias, RFA
"Sevco is a high-impact solution that was quick to configure and delivered extremely quick time-to-value. Having a comprehensive understanding of our assets has really helped us to maximize the investments of my existing tools."
Cecil Pineda, R1 RCMChief Information Security Officer
"Visibility into device inventory is foundational to every security program. It’s challenging to ensure that information stays accurate and updated. Sevco quickly delivers this information to the team and gives us the ability to confidently take action and make informed decisions."
Everett Bates, EverviewChief Information Security Officer
“Sevco gives us the ability to help our customers identify gaps that they did not know existed, giving them an accurate picture of their real attack surface. Partnering with Sevco has delivered immediate value, enabling us to scale quickly and deliver important, foundational security services to our customers across the world.”
Jason Norred, Solutions IIChief Information Security Officer
The latest in asset intelligence.

Sevco is committed to ensuring vulnerability management programs have the structure they need to operate at scale, and we will always normalize and enrich all vulnerabilities with whatever standards emerge.
Brian Contos chats with Steve Lodin, Vice President of Information Security at Sallie Mae, about the importance of exposure management beyond traditional vulnerability scanning.

Platforms that centralize assets, vulnerabilities, and threat intelligence into one place are driving more effective exposure management.
Brian Contos and Brandon Pinzon, former CSO at the Argo Group, discuss why effective exposure management is about more than just identifying CVEs or patching known issues.
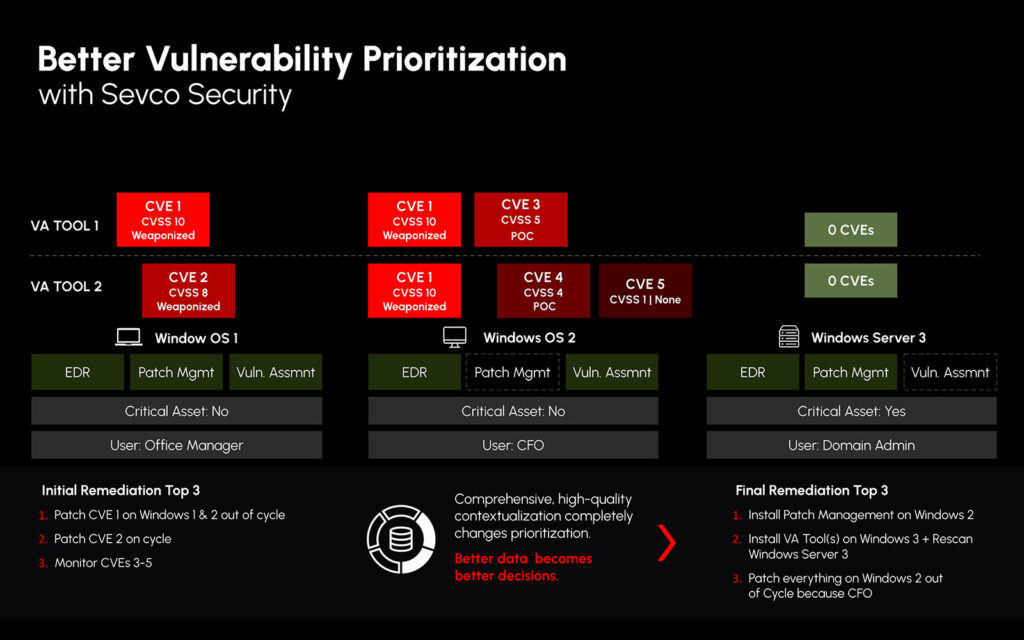
Platforms that centralize assets, vulnerabilities, and threat intelligence into one place are driving more effective exposure management.
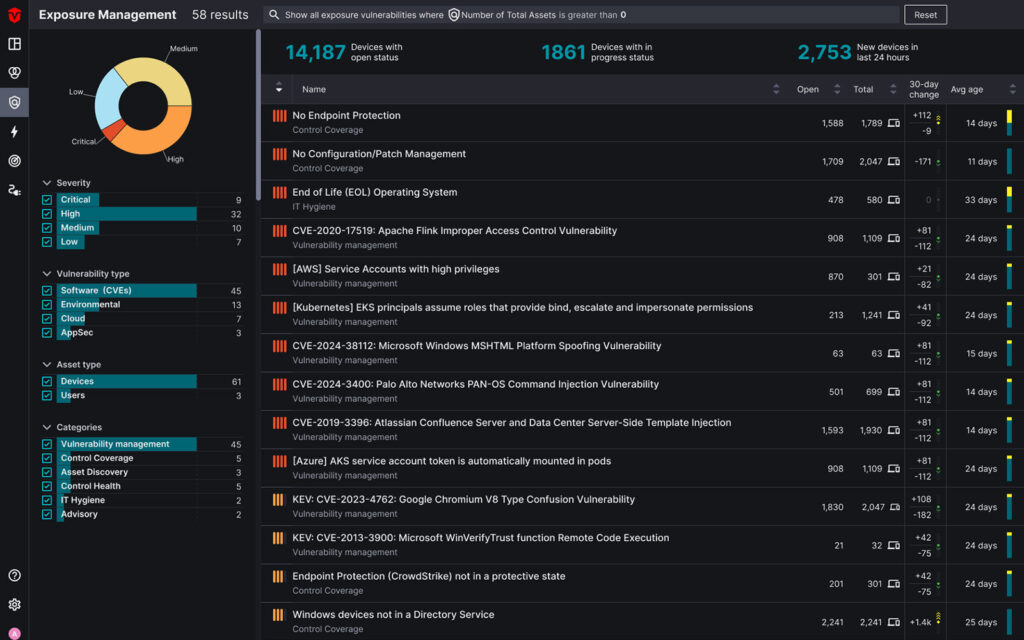
Platforms that centralize assets, vulnerabilities, and threat intelligence into one place are driving more effective exposure management.
Take the next step in securing your assets today
Schedule a one-on-one platform walkthrough to see what Sevco can do for you.
AWARDS
Proud to earn industry trust.