4D User Interface.
Single source of truth for all known and unknown assets.
Presence and state of all assets on the network.
The information swiftly and methodically pushed through each process phase can now be used for accurate visibility and observability of your environment. Our proprietary at-a-glance user interface is how you access and utilize the power of 4D Asset Intelligence.
Highlights of popular features.
Access and manage complete, accurate inventory.
Identify where gaps may exist in the environment.
Discover asset commonality and uniqueness by source.
See within a complex and dynamic environment.
Filter in on the information that matters most to you.
Dive deep into any individual or group of assets.
View specific activities and details of assets.
Geolocate assets anywhere in the world.
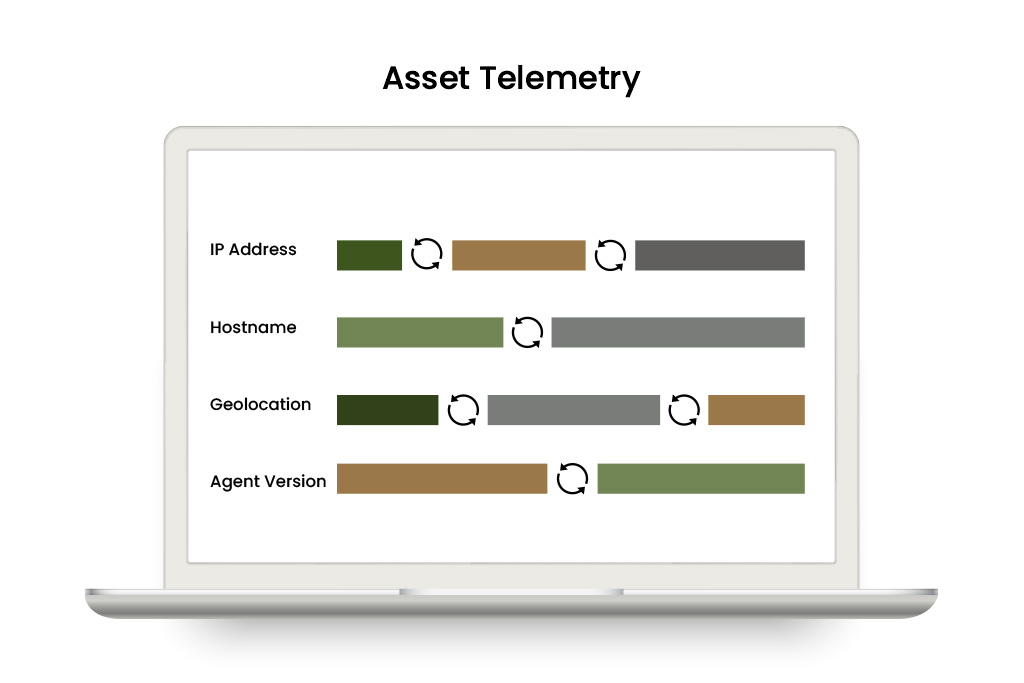
Understand historical change events by asset.
Automate workflows for remediation.
More about the 4D Asset Intelligence platform.
Platform Overview
A thousand-foot view of each stage of the process and how they relate to one another.
Multi-Source Aggregation
Comprehensive visibility of assets by aggregation of your existing systems.

Data Pre-Processing
The standard yet critical step of normalizing, identifying, and prepping the data.
Asset Correlation Engine
Our unique correlation, reconciliation, and deduplication process for maximum accuracy.
4D User Interface
Our proprietary single source of truth for all known and unknown assets on your network.
Data Output
Delivering valuable real-time information and insights into your IT infrastructure.
What our customers say about us
The latest in asset intelligence.


EXPLORE THE SEVCO PLATFORM
Easy remote setup.
AWARDS









