Corporate cybersecurity is, in a nutshell, about protecting the business environment. But what if you don’t know about everything in your environment? It’s simple: You can’t protect what you don’t know about.
Despite the most ambitious investments in security tools, if asset inventory is stale, out of date, or missing information, your company has incomplete security coverage. Of course, IT and security professionals agree that asset inventory is a foundational element of a company’s security program. But, at any given time, companies are experiencing incomplete security coverage with upwards of 19% of assets that have missing or stale security controls like endpoint protection and patch management.
This incomplete-inventory-phenomena has companies operating at elevated security risk levels because those unknown assets are giving attackers a way in.
Inventory challenges
Why are asset inventory efforts failing? The challenges boil down to two critical pain points:
- The first is siloed systems. Individual tools report inventory based on their limited perspective of the environment. No single system provides a comprehensive view of a company’s assets.
- The second is maintaining accuracy in a dynamic environment. Current approaches to asset inventory rely on periodic snapshots but miss critical details of the changes between them.
Fixing the inventory problem with Sevco Security
Sevco Security arms you with an accurate, real-time view of your assets, which makes it easy to assess if they have the appropriate security coverage. You can quickly identify your asset attack surface and resolve gaps in security coverage.
How do we fix the inventory problem? We take a unified view (eliminating the siloed system challenge) and we maintain accuracy so the inventory is always a current reflection of your environment.
Obtaining a unified view of asset inventory
Sevco connects to your existing inventory sources to aggregate and deduplicate the data to deliver a comprehensive inventory. With a truly centralized view, you will have the foundation to understand if you have proper deployment of your existing tools, monitor and track build standards, and most importantly—the solid foundation for your security program: an accurate asset inventory.
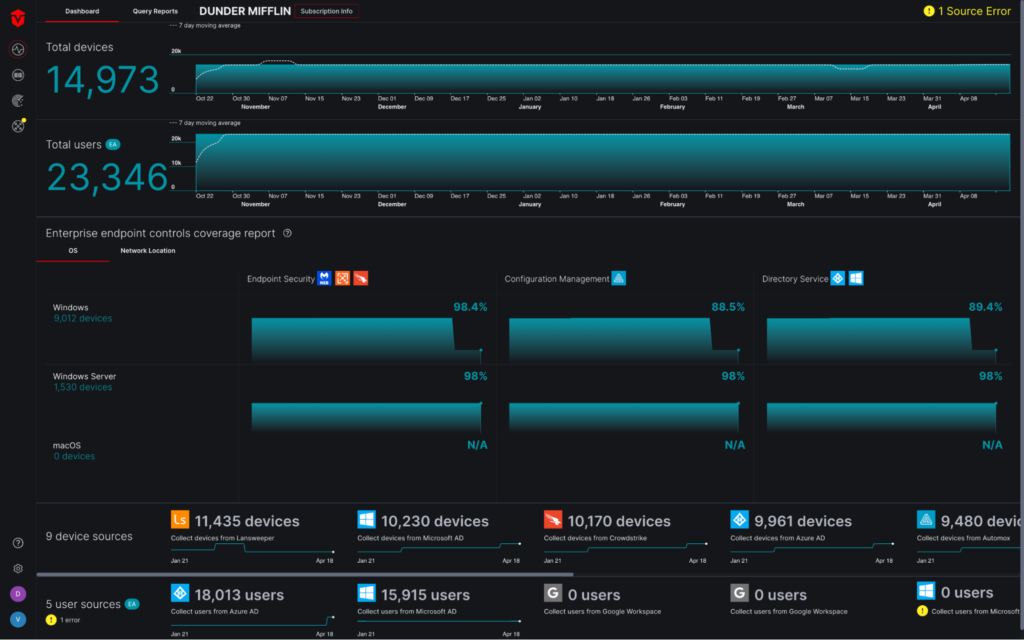
Getting insights into your security coverage
Our attack surface dashboards make it easy for you to quickly answer:
- Do all assets have protection coverage from the security solutions in which our organization has invested?
- When was the last time the security control checked in on each asset?
- Does the coverage execute as expected?
- Which user is associated with the device (and do they represent a higher risk)?
This also empowers companies to manage internal governance and regulatory compliance requirements to monitor and validate that their security investments are fully deployed.
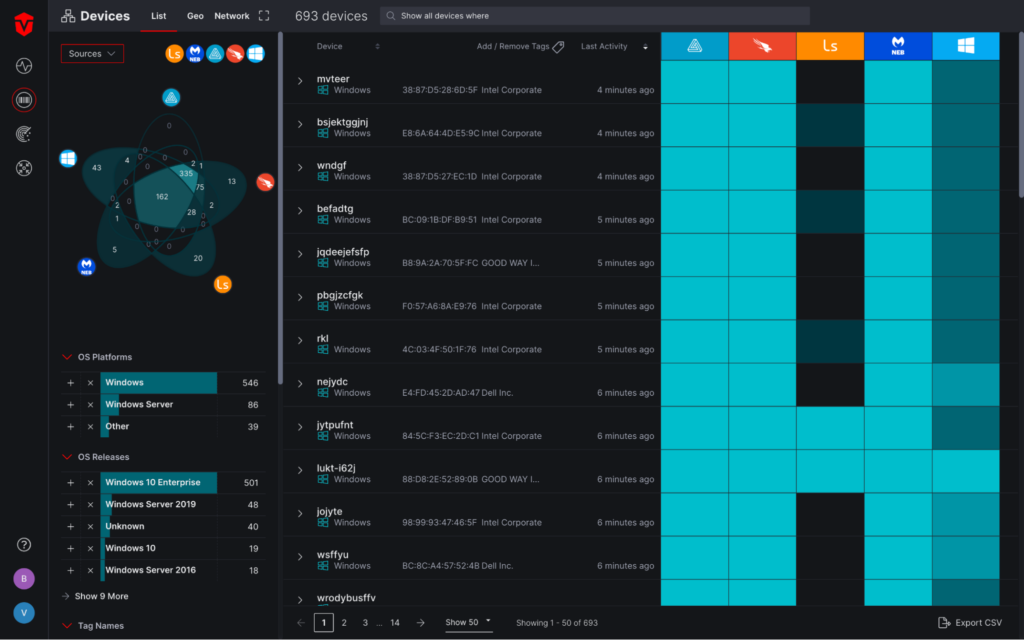
Seeing your timeline trending
Enterprise assets are tracked on a daily trendline empowering IT and security leaders to gain context of what’s typical for their environment and to readily view spikes and outlier activity. Out-of-the-box trending data is automatically captured for total devices, new devices, inactive devices in the last 15 days, total users, and new users.
The trend timeline in each cell provides a visual representation of the last 90 days of its device coverage. Hovering over the timeline gives you a view of your endpoint security coverage details for a specific day.
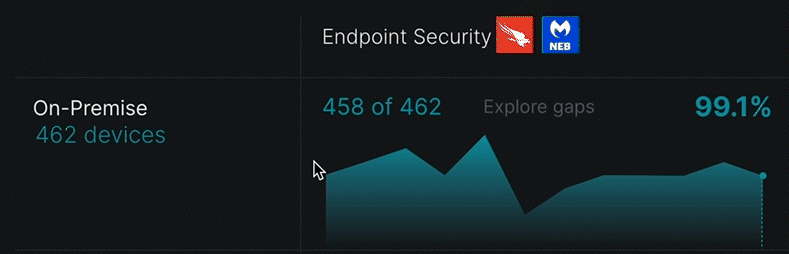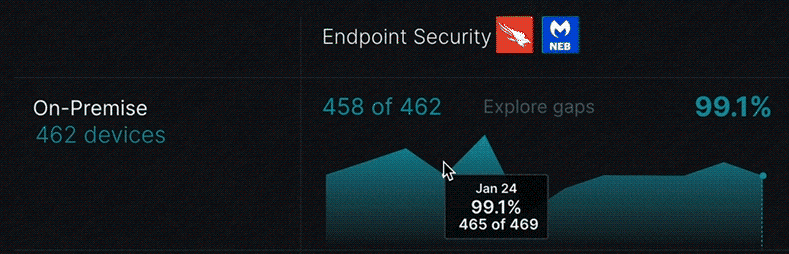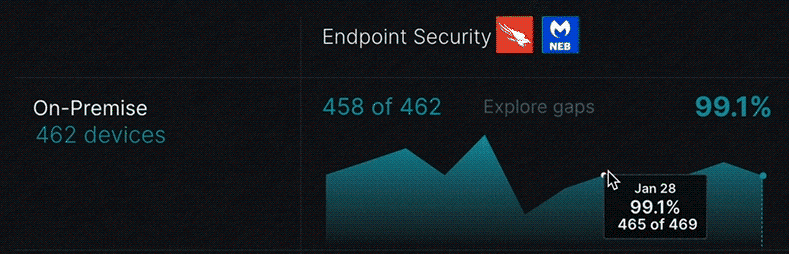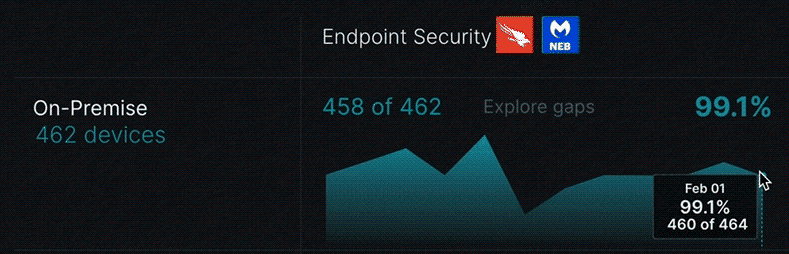
Closing the gaps in security coverage
You can quickly deep dive in the dashboard to explore your security coverage gaps. Link in any cell redirects you to the Device Inventory page where you can view additional information about its corresponding devices.
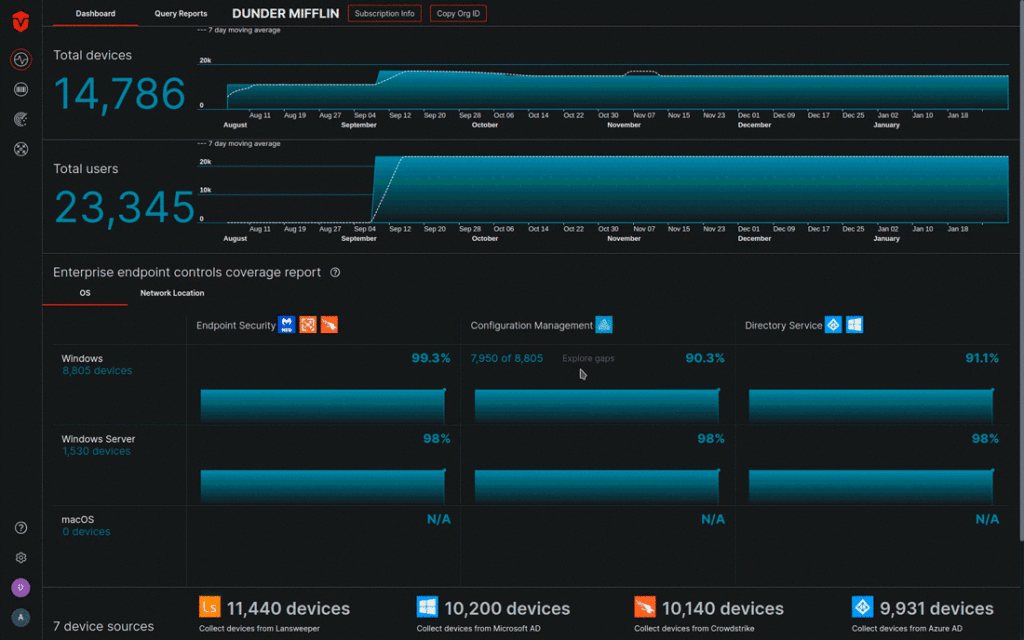
Getting started
To learn more and to get started, visit the Sevco Security home page.
