Vulnerability prioritization is the strategic process of ranking security vulnerabilities based on factors such as potential impact, severity, and likelihood of exploitation. This approach enables security teams to focus their remediation efforts on addressing the most critical vulnerabilities first—optimizing resource allocation and reducing overall risk exposure.
Having a complete and real-time view of all assets, identities, configurations, and vulnerabilities is critical to security operations. But it is the visualization of the dynamic interconnected relationship between all of this rich data that is truly valuable—and actionable. We call this intelligence the Sevco Asset Graph.
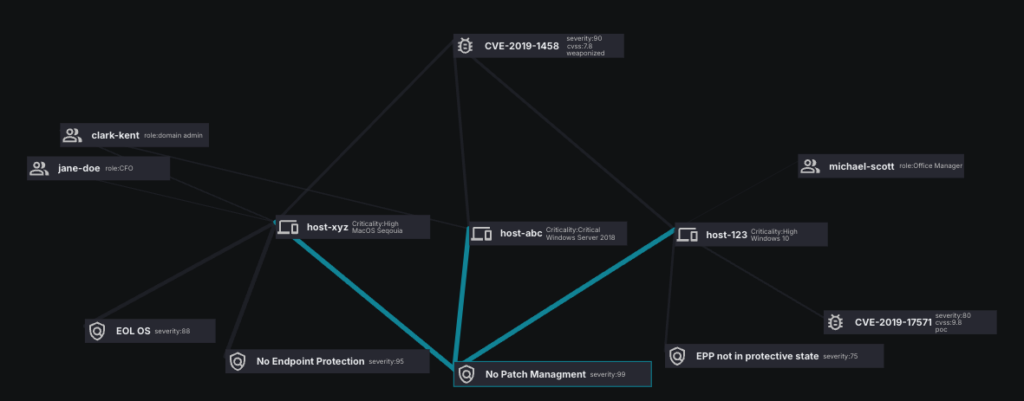
This intelligence provided by the asset graph is what enables truly effective and comprehensive vulnerability prioritization within the Sevco Exposure Assessment Platform.
In this example, we have three devices, two Windows OS machines, and one Windows Server. You can see the associated asset criticalities and the vulnerabilities that have been pulled in from those machines via a vulnerability assessment tool (VA Tool 1). There are two unique CVEs: CVE1 and CVE3.
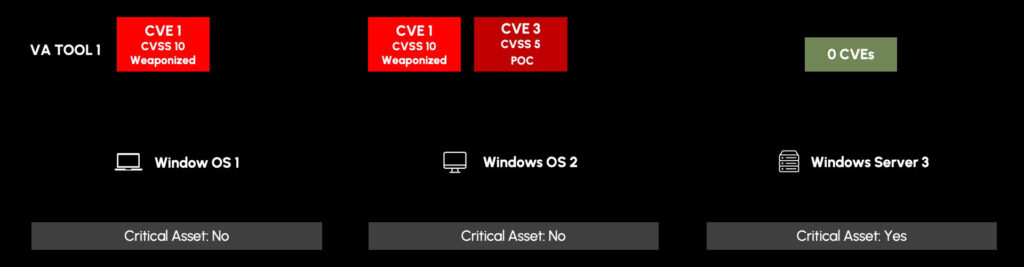
Looking at this data, a vulnerability analyst may think the vulnerability prioritization and remediation actions are straightforward.
- Patch CVE1 on Windows OS 1 off-cycle
- Monitor CVE3 on Windows OS 2
However, it’s becoming more common for vulnerability management teams to run more than one vulnerability assessment tool. After bringing in vulnerability data from a second vulnerability assessment tool (VA Tool 2), we now see CVE2, CVE4, and CVE5 that need to be prioritized against the initial results from VA Tool 1.
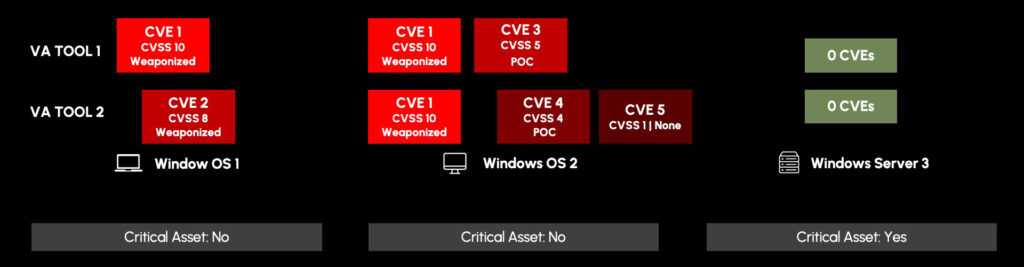
Let’s take a look and see what we should do now. After consolidating the results and being presented with more data, a vulnerability analyst may conclude:
- Patch CVE1 on Windows OS 1 and Windows OS 2
- Patch CVE2 on Windows OS 1 on-cycle
- Monitor CVE 3, CVE4, and CVE5 due to the low severity level and the maturity of the exploit is still in proof-of-concept
The above actions take care of vulnerability prioritization from a pure vulnerability perspective. But let’s see if incorporating asset context changes vulnerability prioritization and the actions a vulnerability analyst may want to take.
Each of these devices should have three critical security controls, endpoint agents, patch management agents, and they should be scanned for vulnerability assessment.
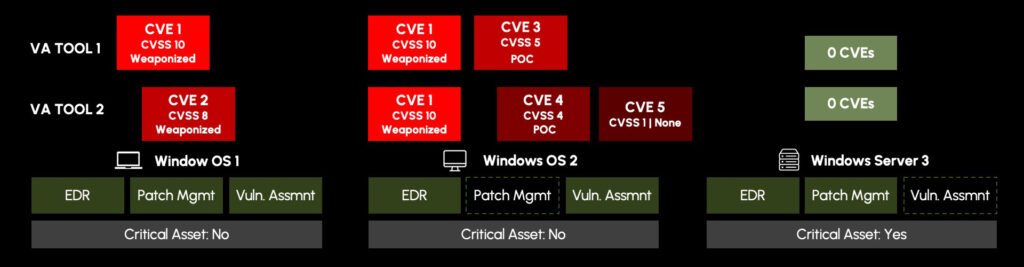
If we look at Windows OS 2, we noted that it has a critical vulnerability and yet we can see that it’s missing patch management. Without the installation of a patch management agent, any remediation efforts would be futile. Without patch management, there ‘s no way for an IT team to push a patch to the impacted device. And research shows that a staggering 60% of breaches occur because of vulnerabilities that go unpatched—even when a fix is available1.
And if we look at Windows Server 3, it’s actually been missed entirely from vulnerability assessment scanning. What was believed to be a system without any vulnerabilities, in reality, could be impacted by numerous CVEs, but was hidden from view. If Windows Server 3 was impacted by CVE 1, a critical, weaponized vulnerability, it would very likely change the vulnerability prioritization strategy.
Adding identity data further increases the complexity and highlights the necessity of having the detailed interconnected relationship data of assets, identities, configurations, and vulnerabilities.
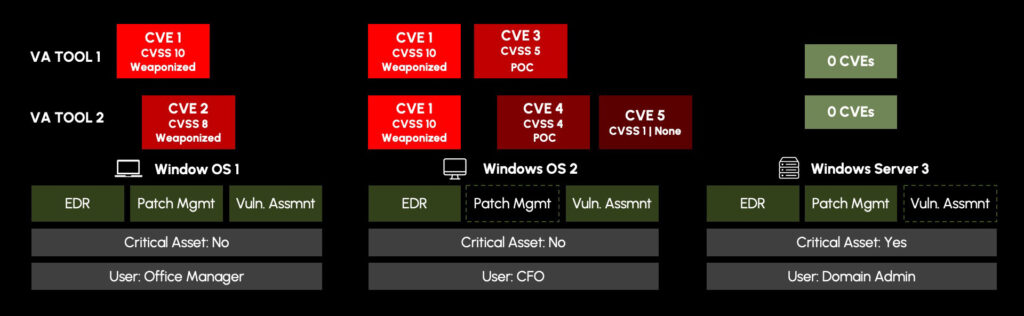
When we layer in user data, we can see Windows OS 1 is associated with the office manager. However, the associated user on Windows OS 2 is the CFO. Having a board-level executive with a system that is impacted by critical CVEs that can’t be remediated (remember, this is the system missing patch management) is a significant risk exposure. Even more serious in terms of risk exposure is the critical Window server associated with a domain admin that has been completely missed in vulnerability scans. There is no way to know how many CVEs and the criticality of the CVEs that may be impacting the system.
As we’ve shown with this example, Sevco provides organizations with better data to drive better, more impactful decisions. Having the full context of the vulnerabilities, device configurations, and the users associated with them completely changed the vulnerability prioritization strategy.
Based on all of the data presented, let’s see what a vulnerability analyst would now give as the final remediation recommendations. They’ve changed quite a bit from the initial recommendation.
- Recommendation #1: Install patch management on Windows OS 2. Without the patch management agent, the remediation efforts to resolve CVE1 on Windows OS 2 will be futile.
- Recommendation #2: Add Windows Server 3 to the vulnerability assessment tool(s) and ensure it is being scanned to understand if there are truly no vulnerabilities associated with the system or determine if vulnerability prioritization needs to be re-evaluated.
- Recommendation #3 : Patch Windows OS 2 off cycle as the associated user is the CFO.
As you can see, the Sevco Asset Graph powers truly comprehensive vulnerability prioritization to provide the intelligence you need to make strategic decisions based on your organization’s unique characteristics and requirements. By looking beyond CVEs and including the dynamic data associated with assets, identities, configurations, and vulnerabilities you can take a much more holistic approach to vulnerability prioritization. Better data drives better decisions.
