The Only Platform for Your Continuous Threat Exposure Management Program.
Assess your attack surface, prioritize threats, and remediate
exposures—all from a single tool. Sevco unifies your siloed data, processes,
and teams to enable proactive exposure management across the enterprise.
How Sevco Supports Customers on their CTEM Journey:
- Generates a comprehensive asset inventory and relational map of your entire attack surcace—applications, devices, users, and vulnerabilities.
- Unifies, normalizes, prioritizes, and validates all types of exposures—missing security controls, misconfigurations, CVEs, Cloud and AppSec vulnerabilities.
- Facilitates action to resolve critical risk and validate that exposures are resolved—confirming resolution beyond the closure of tickets.
How Sevco’s Exposure Management
Helps Security Teams
Gain Full Visibility and Control Over Cyber Assets to
Strengthen Security Defenses
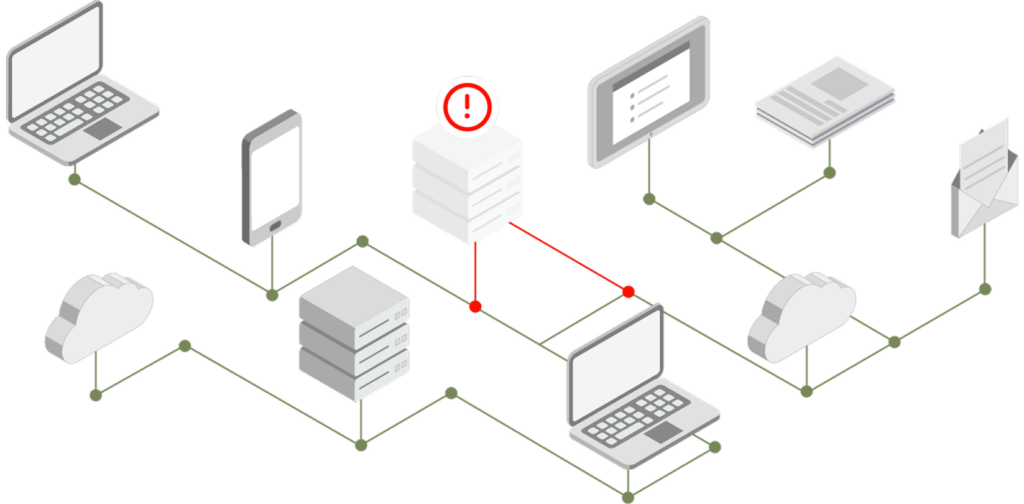
Scope Your Attack Surface.
Uncover your assets through continuous and real-time data aggregation, deduplication, and correlation from 1000+ IT, security, and home grown tools.
Discover Your Vulnerabilities.
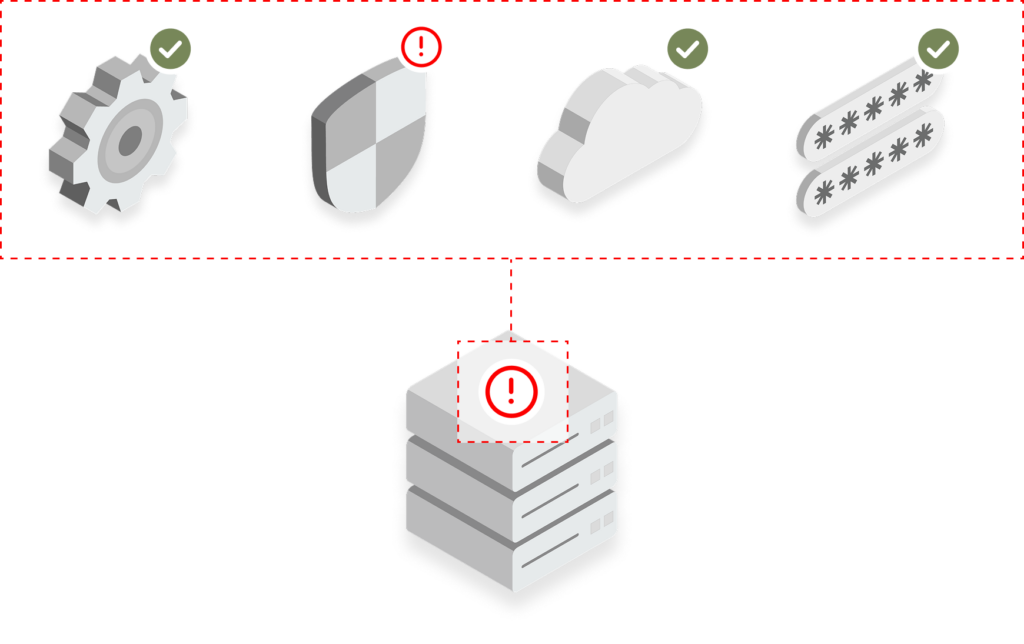
Integrate with all of your vulnerability sources to discover the full scope of your exposures—missing security controls, misconfigurations, CVEs, Cloud, AppSec—and reveal hidden risks.
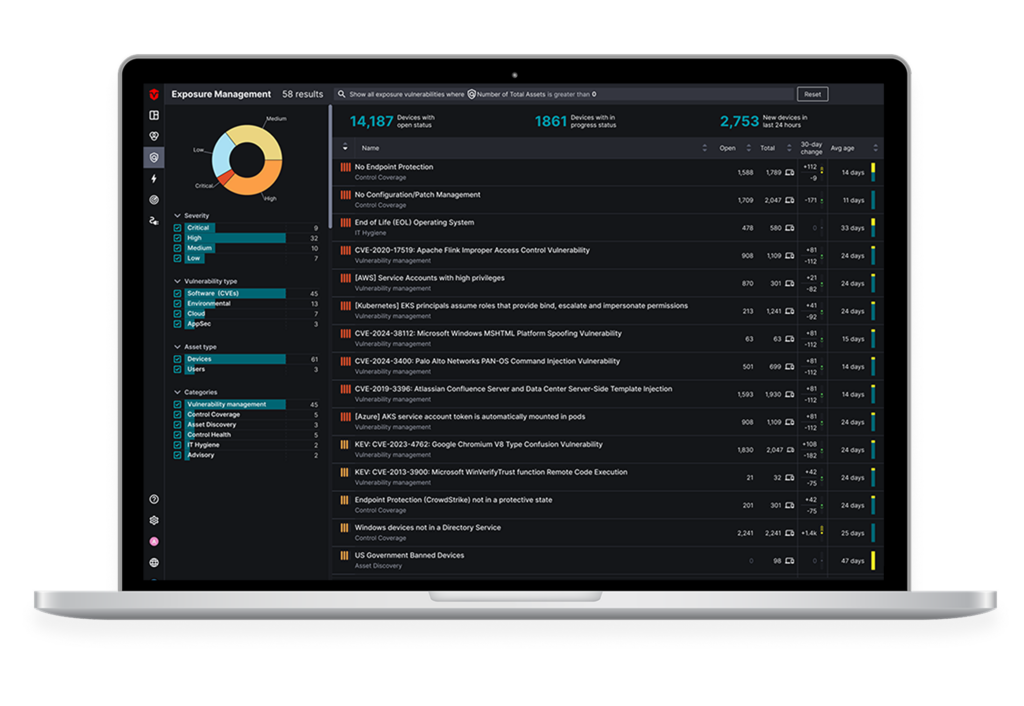
Prioritize Your Risk.
Normalize and standardize the quantification of risk across different types of exposures. Layer in asset inventory, threat intelligence, and business context for custom rankings.
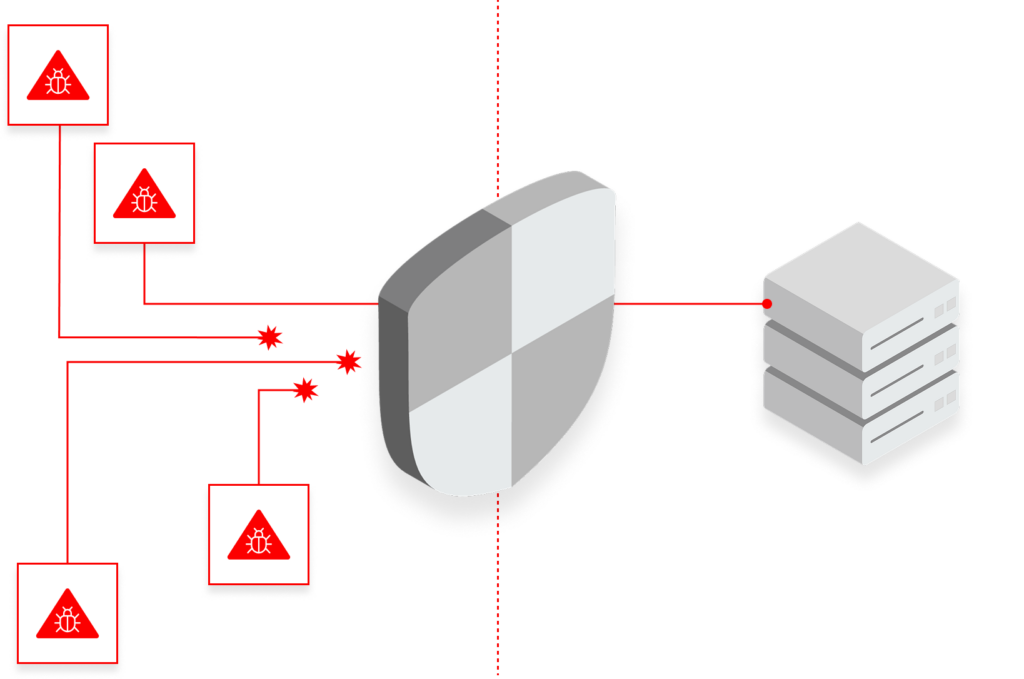
Validate Your Exploitability.
Leverage the full context of the attack surface to validate prioritization. Ensure that the exposures that matter the most —those that are exploitable with high business impact—are remediated.
Mobilize Your Findings.
Set custom actions to automate remediation, enrich critical IT infrastructure with Sevco’s data, validate the resolution of risk, and report on the health of your CTEM program.
How is Sevco different?

Always On.
Continuous monitoring of your attack surface ensures an accurate picture of the attack surface—in any given moment. Every change is perfectly captured without manual intervention.
Entirely Unified.
All of your security data—one tool to manage it. Sevco moves beyond siloed infrastructure, and gives you the holistic view of your attack surface.
Normalized Risk.
Risk scoring for all of your exposures—missing security controls, misconfigurations, CVEs, Cloud and AppSec vulnerabilities—are normalized on the same scale for unified prioritization.

ASSET
Asset Title
Learn how to enhance visibility, reduce risk, and build a stronger security posture with proactive strategies and best practices. Download now to stay ahead of evolving cyber threats.

ASSET
Asset Title
Learn how to enhance visibility, reduce risk, and build a stronger security posture with proactive strategies and best practices. Download now to stay ahead of evolving cyber threats.

ASSET
Asset Title
Learn how to enhance visibility, reduce risk, and build a stronger security posture with proactive strategies and best practices. Download now to stay ahead of evolving cyber threats.

ASSET
Asset Title
Learn how to enhance visibility, reduce risk, and build a stronger security posture with proactive strategies and best practices. Download now to stay ahead of evolving cyber threats.

ASSET
CTEM: The Foundation of Modern Security
Continuous Threat Exposure Management (CTEM) programs have emerged as a revolutionary approach to addressing exposures, enabling organizations to manage risk holistically and continuously. Read this digital whitepaper to learn how you can build a more resilient security posture.
Key Exposure Management Features
Asset Intelligence.
Comprehensive asset inventory —applications, devices, users, and vulnerabilities—and the relationships within and between them.

Vulnerability Management.
The full context of your attack surface applied to vulnerability prioritization—enabling more efficient remediation.

Validated Remediation.
Prove that critical exposures are actually resolved via a remediation feedback loop— going beyond the closure a ticket.
What do our customers have to say?
Take your vulnerability managment to the next level
Reduce risk exposure by prioritizing and remediating CVEs and environmental vulnerabilities like missing agents. Confirm remediation efficacy to improve security processes and reduce exposure.
AWARDS
Proud to earn industry trust.














