Discover Assets. Map Relationships.
Fix Control Gaps.
Generate a complete asset inventory of applications, devices, users, and vulnerabilities –
and the relationships between them. With Sevco’s asset intelligence, customers proactively
manage the deployment and configuration of security controls to reduce attack surface risk.
How Sevco’s Cyber Asset Attack Surface
Management helps Security Teams
Asset Intelligence Provides Comprehensive Data on Cyber Assets
to Strengthen Security Defenses
Complete Visibility.
Uncover your assets through continuous and real-time data aggregation, deduplication, and correlation from 1000+ IT, security, and home grown tools.
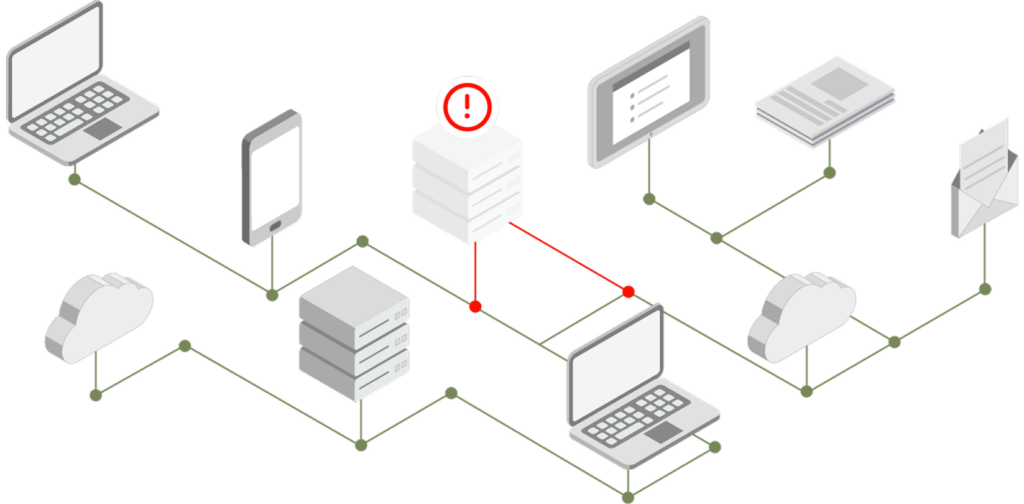
Connected Inventory.
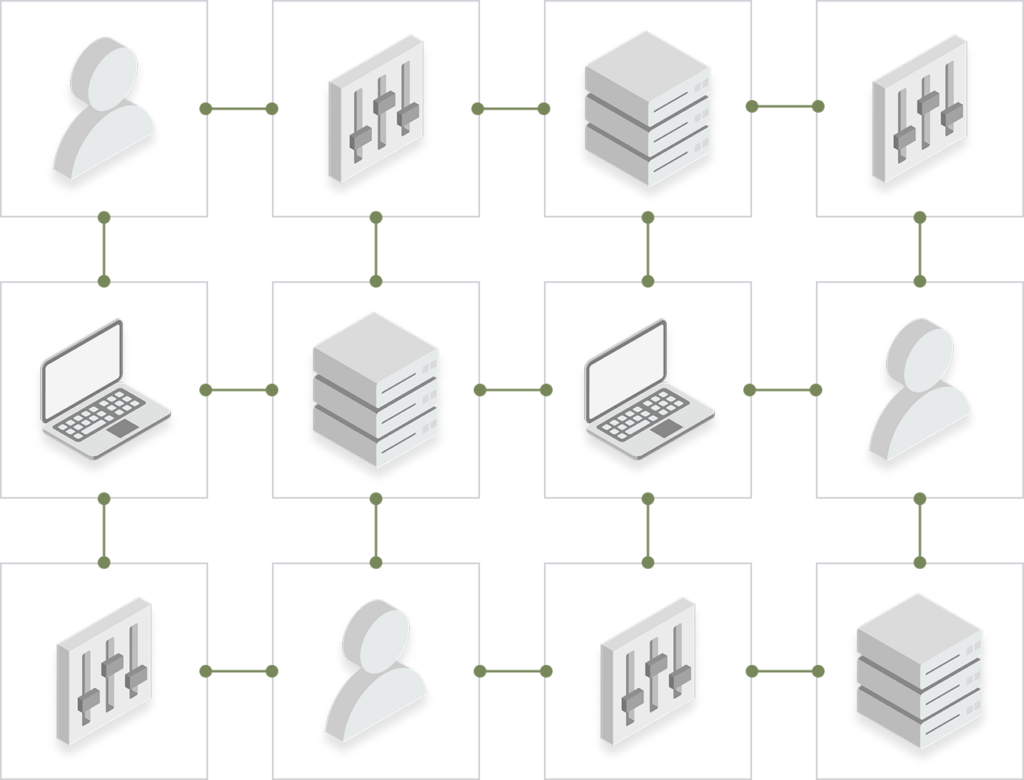
Visualize the relationships within and between your assets – applications, devices, users, and vulnerabilities – and analyze gaps in your security posture.
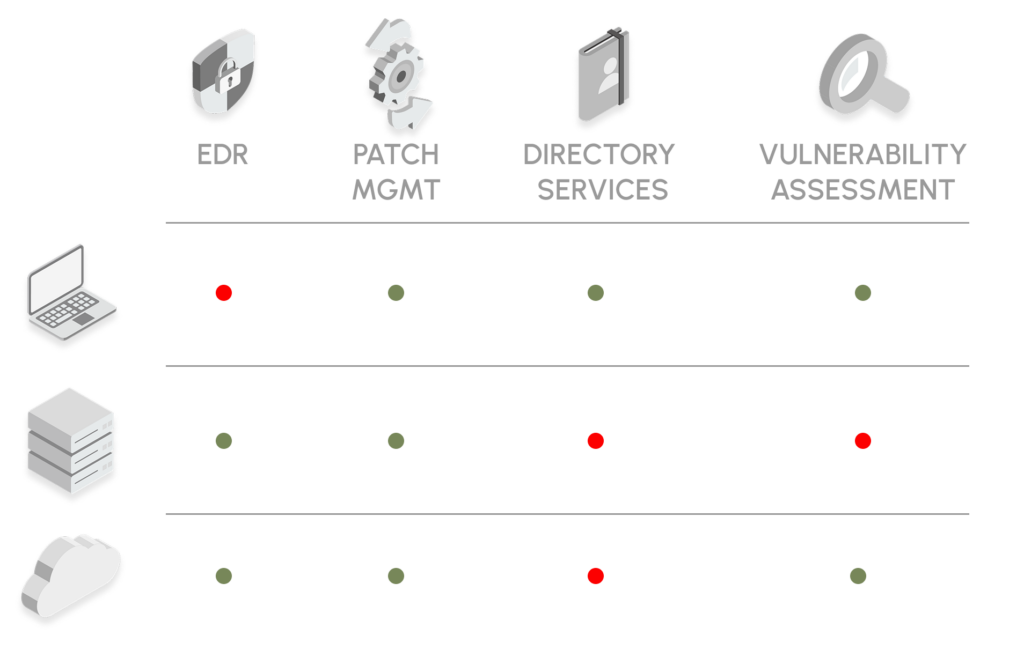
Compliant Assets.
Enforce required policies, configurations, and controls to proactively reduce risk across the attack surface.
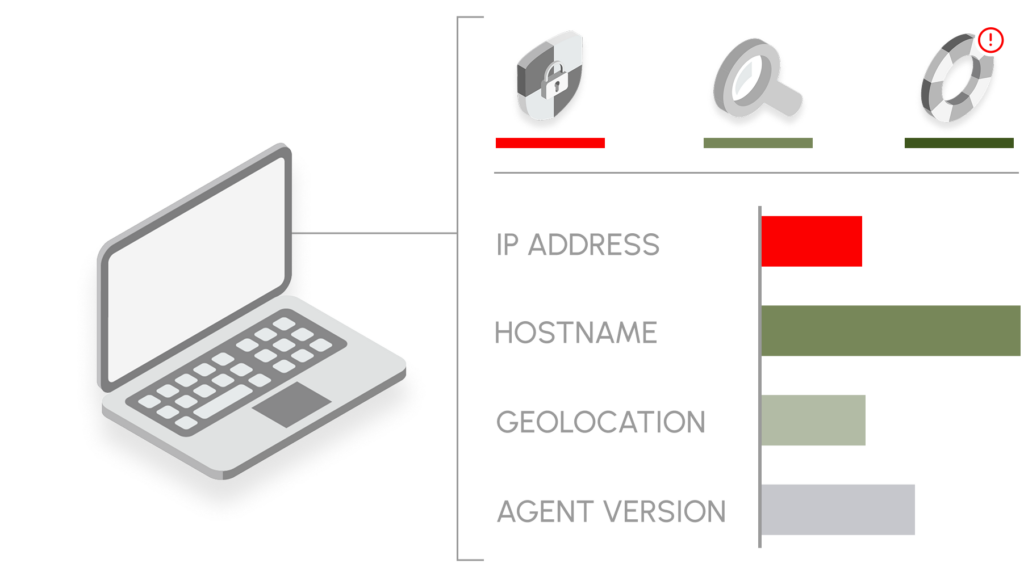
Enriched Data.
Utilize outbound integrations to enrich critical IT infrastructure – CMDBs, SIEMs, and ITSMs – with the full context of Sevco’s asset intelligence and inventory.
How is Sevco different?

Ease of Deployment.
Our best-in-class CAASM solution aggregates, correlates, and deduplicates data from 1000+ tools via API to produce an accurate asset inventory in minutes.

Fully Autonomous.
Our asset inventory is continuously refreshed to ensure an accurate picture of the attack surface—in any given moment. Every change is perfectly captured without manual intervention.

Built for Scale.
Our cloud-native and multi-tenant architecture allows us to serve customers of any size without concerns of performance degradation.

ASSET
Asset Title
Learn how to enhance visibility, reduce risk, and build a stronger security posture with proactive strategies and best practices. Download now to stay ahead of evolving cyber threats.

ASSET
Asset Title
Learn how to enhance visibility, reduce risk, and build a stronger security posture with proactive strategies and best practices. Download now to stay ahead of evolving cyber threats.

ASSET
Asset Title
Learn how to enhance visibility, reduce risk, and build a stronger security posture with proactive strategies and best practices. Download now to stay ahead of evolving cyber threats.

ASSET
Asset Title
Learn how to enhance visibility, reduce risk, and build a stronger security posture with proactive strategies and best practices. Download now to stay ahead of evolving cyber threats.

ASSET
The Criticality of Security Asset Invenory
A security asset inventory requires accuracy far beyond what an IT team needs. It must contain all the assets a security team is accountable for protecting. Learn about the different approaches to security asset inventory strategies in this guide.
Key CAASM Features

1000+ Integrations.
Data ingestion via API integrations to your IT, Security, and home built solutions.

Security Inventory.
Comprehensive asset inventory—applications, devices, users, and vulnerabilities.
Asset Graph.
Mapping the relationships within and between your asset to scope your attack surface and the exposures within it.
What do our customers have to say?
Take your vulnerability managment to the next level
Reduce risk exposure by prioritizing and remediating CVEs and environmental vulnerabilities like missing agents. Confirm remediation efficacy to improve security processes and reduce exposure.
AWARDS
Proud to earn industry trust.













