Today, we’re diving into the evolving landscape of vulnerability management—how traditional approaches have been challenged by expanding attack surfaces, and why exposure assessment platforms (EAPs) are emerging as the future of robust security operations.
We’ll start by revisiting the history of vulnerability assessment tools, examine the impact of attack surface expansion, and explore how Gartner shaped the industry’s response with Continuous Threat Exposure Management (CTEM). Finally, we’ll break down how exposure assessment platforms are consolidating critical security functions to enable more effective risk management.
A Decade of Change: From Traditional Vulnerability Management to a New Era
Ten to fifteen years ago, securing the attack surface was significantly more straightforward. Organizations primarily focused on on-premise assets—endpoints and servers. At the time, vulnerability assessment tools (Tenable, Rapid7, Qualys, etc.) could perform network scanning, detect assets, and identify Common Vulnerabilities and Exposures (CVEs) to be patched. This process worked well in a world where IT infrastructure was largely centralized.
Then everything changed—a new age of digital work evolved incredibly quickly. The rise of SaaS applications, collaboration platforms like Slack and Google Workspace, and the explosion of cloud services introduced new security challenges. The shift to remote work during the pandemic only accelerated these trends, expanding the attack surface beyond traditional network perimeters. Security teams suddenly found themselves managing risk across mobile devices, laptops, cloud environments, personal home networks, and APIs—leading to a fragmented and increasingly complex landscape.
The Expanding Attack Surface: More Assets, More Vulnerabilities, More Complexity
With this expansion of IT environments, the number and variety of assets requiring security oversight has grown dramatically. It is no longer just about endpoints and servers—security teams now have to account for mobile and identity, third-party risk, IoT, SaaS applications, and the cloud. In addition to these multiple asset types, organizations need to understand the context related to the assets including associated users, installed or missing applications, etc.
This shift exposes a fundamental limitation of legacy vulnerability assessment tools: they aren’t designed to track or assess the broad range of assets now critical to modern enterprise operations.
In addition to the expanding attack surface, the vulnerability problem has also been compounded. The number of CVEs has surged in recent years, overwhelming security teams with a growing backlog of issues to address. Meanwhile, these same security teams need to look beyond CVEs to new classes of exposures—such as misconfigurations or missing security controls coverage, outdated software, end-of-life (EOL) systems, and more—which have become just as, if not more, critical to an organization’s security posture.
Cloud Security Posture Management (CSPM) and Application Security Posture Management (ASPM) add further complexity. Traditional vulnerability assessment tools, built for less complex and less dynamic environments, are struggling to keep pace.
A Market Shift: The Rise of New Security Categories
As these challenges have grown, new vendor categories have emerged to address critical gaps in asset visibility and vulnerability management:
- Cyber Asset Attack Surface Management (CAASM): Addresses the asset inventory problem by consolidating and deduplicating data from multiple security tools to create a multi-sourced inventory..
- Vulnerability Prioritization Tools (VPT): Enables security teams to focus on the most pressing risks by quantifying the risk associated with CVEs for prioritization and and remediation.
- External Attack Surface Management (EASM): Provides visibility into external-facing assets such as websites and IPs that attackers can exploit.
Sevco Security entered the CAASM space in 2020 to tackle one of security’s most fundamental needs—a real-time asset inventory that provided organizations with a more accurate, comprehensive picture of the presence and state of assets in their environment. This inventory can tell security teams whether those assets are missing from critical security tools or in an unprotected state because of misconfigurations. From this foundation, the natural extension of Sevco’s capabilities was into vulnerability prioritization, enabling security teams to map vulnerabilities like CVEs to their asset inventory, in addition to providing exploit intelligence and business context to more effectively reduce risk.

The Fragmentation Problem: Siloed Security Solutions Create More Work, Not Less
Despite these innovations, a fundamental problem has remained: security teams now have more data, but it is spread across multiple tools that didn’t communicate with one another. Instead of simplifying risk management, this siloed approach increases operational burden. Organizations need a way to unify asset inventory, vulnerability management, external threat context, and risk prioritization into a cohesive strategy.
Enter Continuous Threat Exposure Management (CTEM).
The CTEM Framework: A Blueprint for Proactive Security
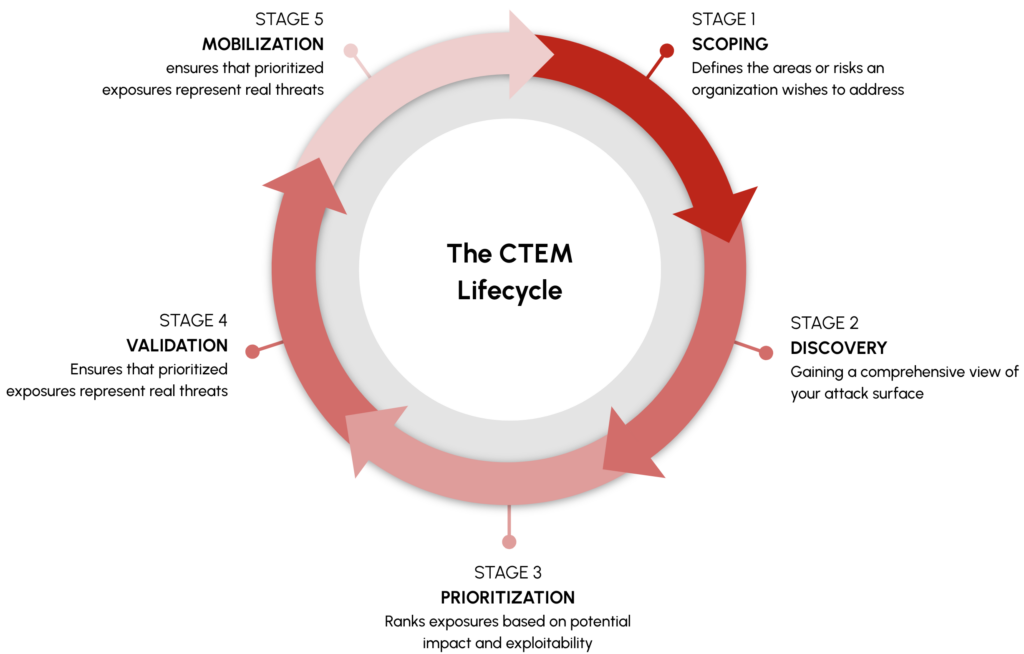
In 2022, Gartner introduced Continuous Threat Exposure Management (CTEM) which is a framework that offers organizations the ability to continuously identify, assess, prioritize, validate, and remediate risks across all assets. CTEM programs help organizations to address these challenges with five pillars:
- Scoping – Defining the organization’s assets and threat landscape.
- Discovery – Identifying vulnerabilities and misconfigurations across the environment.
- Prioritization – Assessing and ranking risks based on potential impact.
- Validation – Simulating and testing threats to confirm real-world exposure.
- Mobilization – Implementing remediation actions and monitoring improvements
The CTEM framework has provided the security industry with a much-needed structured approach to managing risk. However, it also underscores the need for a new type of technology—one that can bring all these elements together. Many organizations are now turning to Exposure Assessment Platforms (EAP) to help drive these programs.
The Emergence of Exposure Assessment Platforms (EAPs)
In 2024, Gartner took the next step by consolidating multiple security categories—Vulnerabhttps://www.sevcosecurity.com/sevco-glossary/exposure-assessment-platform-eapility Assessment (VA) and Vulnerability Prioritization (VPT)—into a single category: Exposure Assessment Platforms (EAPs).
An EAP empowers an organization to efficiently address its most critical security gaps by enabling the prioritization of vulnerabilities based on real-world impact. The 2024 Gartner® Hype Cycle™ for Security Operations identified exposure assessment platforms as marking a significant advancement in security technology.
As we mentioned above, today’s security teams manage a vast array of assets across their environments. And as we have shown, traditional vulnerability management tools often fall short in providing the comprehensive visibility and proactive risk mitigation required to protect data from such a diverse set of sources.
EAPs represent the natural evolution of security operations, designed to:
- Unify security data from vulnerability assessment tools, CAASM solutions, EASM insights, and threat intelligence feeds.
- Prioritize exposures holistically, accounting for misconfigurations, identity risks, and external exploitability—not just CVEs.
- Enable effective remediation by providing security teams with clear, actionable intelligence.
This shift signals a move away from fragmented, tool-specific solutions toward comprehensive risk management platforms that integrate asset visibility, vulnerability assessment, and risk prioritization into one cohesive solution.
Sevco’s Vision: A Unified Approach to Exposure Management
At Sevco Security, we believe an accurate, dynamic asset inventory is the foundation of any effective security program. Without a real-time understanding of what assets exist, where they reside, and who owns them, it’s impossible to manage risk effectively.
We’ve built the Sevco Exposure Assessment Platform from our industry-leading CAASM solution. We believe that consolidating data from your security tools into a single dashboard enables you to make better decisions to proactively reduce risk. Importantly, Sevco consolidates all types of vulnerabilities into one platform. Coupling CVEs—mapped to assets to gain comprehensive visibility into traditional software vulnerabilities and the risks they pose—with what we might call “CAASM vulnerabilities” like missing or misconfigured agents, end-of-life systems, shadow IT, and more, provides security teams with a better picture of the state of risks in their environment than any other individual tool. By integrating exposure discovery, risk prioritization, and remediation enablement, we’re helping organizations move beyond traditional vulnerability management and embrace a proactive, exposure-driven approach to security.
What’s Next?
As security teams grapple with the expanding attack surface and the increasing complexity of modern IT environments, the need for consolidation and automation has never been greater. The Sevco platform represents the next frontier in exposure management, providing the comprehensive visibility, exploit and vulnerability intelligence, and automation needed to stay ahead of threats and reduce risk.
If you’re ready to take a proactive approach to managing your attack surface, Sevco can help.
