Cybersecurity is evolving at a rapid pace, and with it comes the need for a more robust approach to managing risk across an ever-expanding attack surface. Continuous Threat Exposure Management (CTEM) is at the forefront of this evolution, offering organizations the ability to continuously identify, assess, prioritize, validate, and remediate risks across all assets. Many organizations are turning to Exposure Assessment Platforms (EAP) to help drive these programs.
In this digital white paper, we’ll explore CTEM, its five foundational pillars, and the technology that supports its implementation. We’ll introduce Sevco and explain how our solution enables organizations to implement and manage their own exposure management programs with all the intelligence they require from a single platform.
An Introduction to CTEM
The Challenge: Everchanging Data = Everchanging Risk
Organizations face a daunting challenge: how to reduce cyber risk in everchanging IT environments while simultaneously managing the increasing volume of exposures and vulnerabilities across the growing attack surface. Traditional approaches like vulnerability management and periodic assessments are no longer sufficient to address the dynamic threat landscape.
The continuously shifting nature of IT assets—new devices, users, configurations, vulnerabilities, and cloud deployments—means that the risks are perpetually evolving. Static, point-in-time assessments fail to keep pace with this flux.
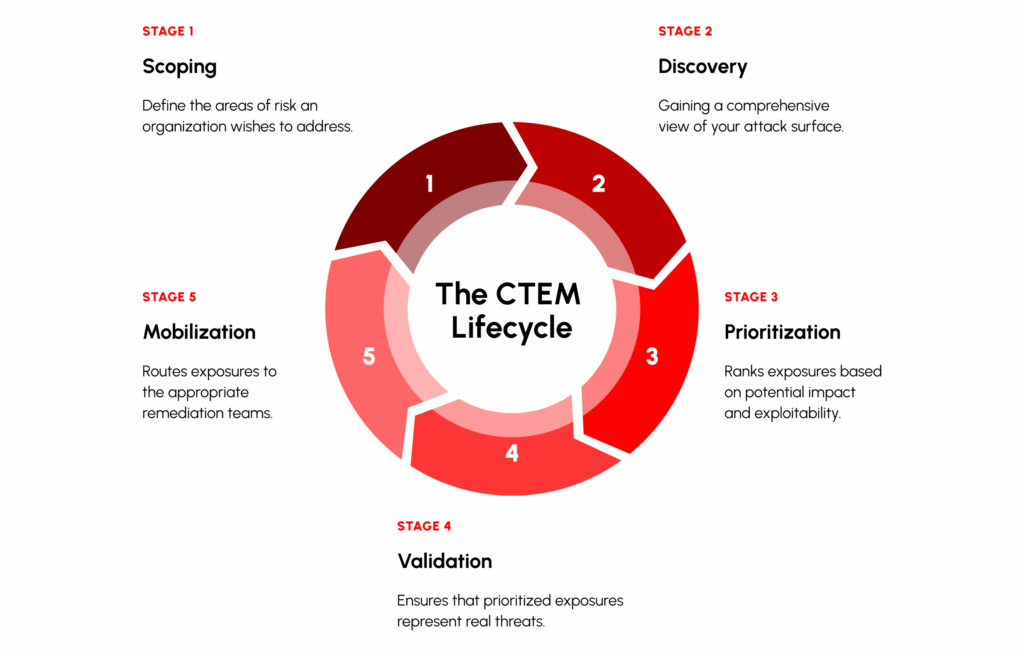
The Five Stages of CTEM
CTEM programs help organizations to address these challenges with five pillars:
- Scoping – Defining the organization’s assets and threat landscape.
- Discovery – Identifying vulnerabilities and misconfigurations across the environment.
- Prioritization – Assessing and ranking risks based on potential impact.
- Validation – Simulating and testing threats to confirm real-world exposure.
- Mobilization – Implementing remediation actions and monitoring improvements
How Can EAPs Help?
Exposure Assessment Platforms (EAPs) provide a centralized, integrated solution to manage these exposures. By consolidating data across diverse tools, EAPs offer real-time insights into an organization’s vulnerabilities and risk posture.
Effective CTEM relies on technology that:
- Provides comprehensive asset visibility
- Prioritizes vulnerabilities based on technical and business context
- Validates risks with real-world simulations
- Mobilizes remediation efforts efficiently and collaboratively
Sevco’s Exposure Assessment Platform
Sevco offers a complete Exposure Assessment Platform, empowering organizations to operationalize their CTEM programs effectively. Sevco helps organizations who have too many issues to address, and too little intelligence on which exposures and vulnerabilities present the greatest risk.
Sevco consolidates comprehensive intelligence needed to more effectively prioritize vulnerabilities for remediation in a single platform. We built flexible, powerful prioritization capabilities and uniquely centralized the greatest risks of all types – CVEs, missing agents, business-critical assets missing security controls – into a single dashboard, prioritized by risk.
CAASM / Inventory (CTEM Scoping)
Many organizations struggle with incomplete and inaccurate asset inventories. Many solutions try to solve this problem, but their inventories continue to fall short, and customers continue to feel the pain of incomplete visibility.
Sevco addresses this through:
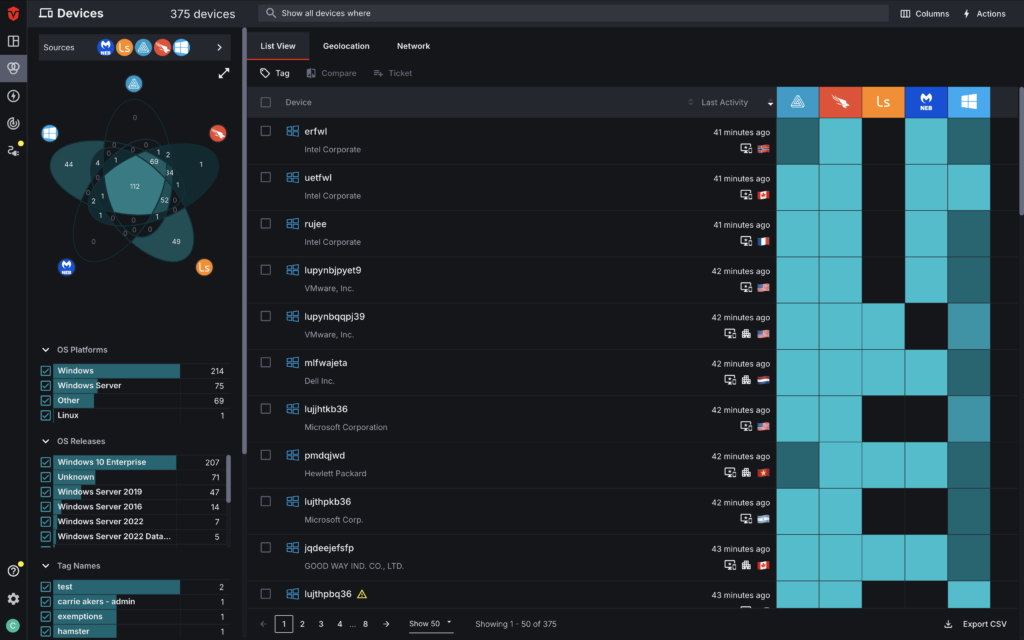
- Aggregation and Deduplication: Sevco integrates with 1000s of existing security tools via API to automatically ingest, aggregate, and deduplicate assets. Our inventory is live, meaning we’re pulling source data and running it through our correlation engine (Sevco’s proprietary data models) in real-time to ensure you always have an accurate picture of the entire attack surface.
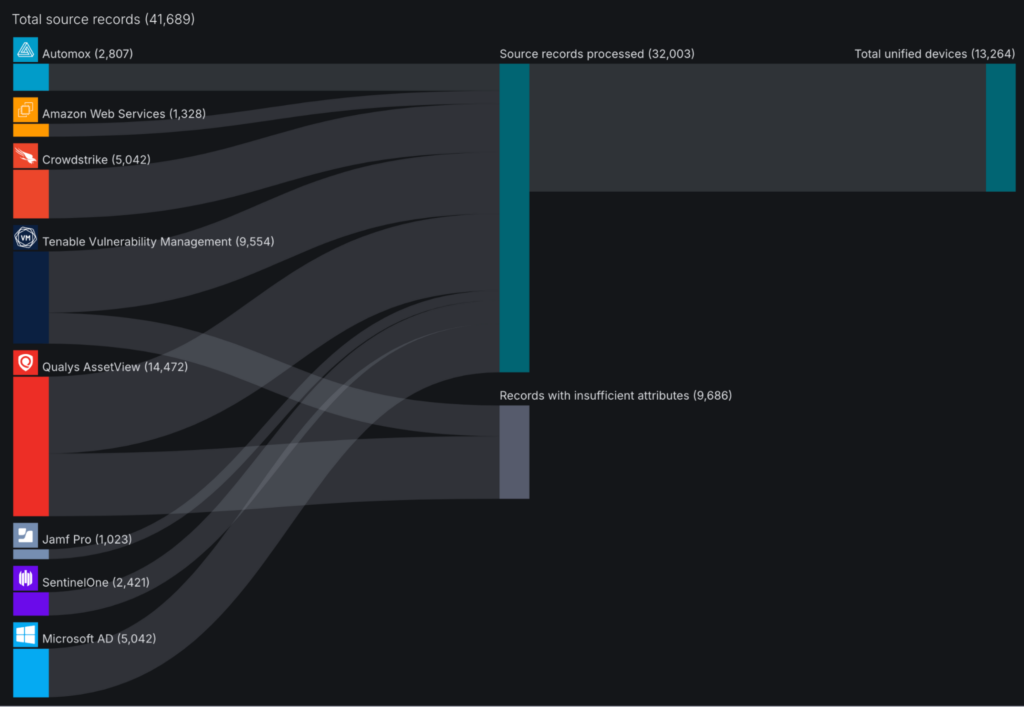
We’ve named our inventory the Security Inventory, because it goes beyond traditional constructs of an asset inventory. At Sevco, we have six classes of assets:
- Devices – laptops, mobile phones, servers, etc.
- Identities – users
- Software – applications hosted on assets
- Vulnerabilities – more than just CVEs, we look at misconfigurations and controls coverage gaps, CSPM vulnerabilities, ASPM vulnerabilities, and traditional software vulnerabilities
- Cloud Assets – VMs, databases, storage buckets, etc.
- Security Controls Coverage – presence and state of critical controls
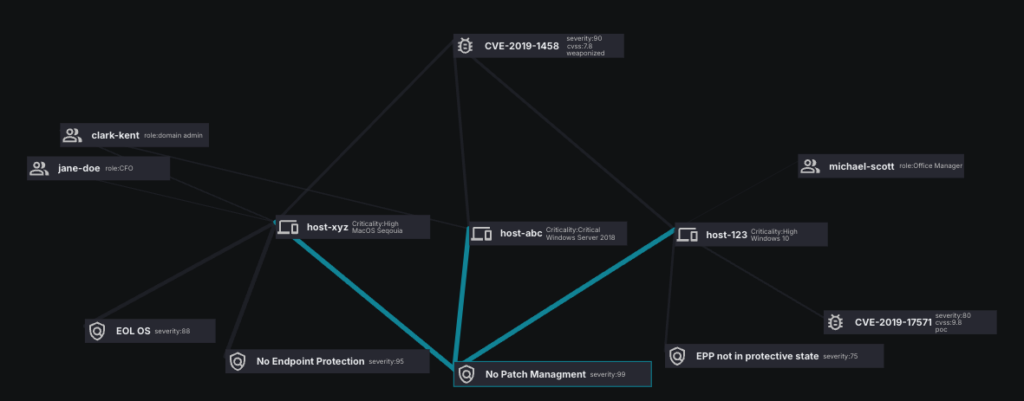
After creating the unique inventory of all six asset classes, we stitch it all together. Think of a web that links devices to their users and vulnerabilities (and more) – at scale across your environment. Every relationship, perfectly mapped and maintained, automatically. We call this the Asset Graph.
- Asset Graph: Relational mapping of the assets that make up the entire attack surface enables holistic visibility and informed decision-making.
- For example, Sevco can show you a critical production server tied to a domain admin user with a misconfigured EDR agent that has a critical, weaponized CVE on it that is unpatched.
Vulnerability Management (CTEM Discovery + Prioritization + Validation)
Discovery of Vulnerabilities
Sevco identifies vulnerabilities beyond traditional CVEs, consolidating insights from:
- CAASM Vulnerabilities: This one is new for the industry – but, we believe that misconfigured and missing security controls need to be identified and prioritized for remediation. Just like CVEs. So, we coined our own term, CAASM Vulnerabilities. Within Sevco, you can see all the devices that are mis / missing configurations e.g. missing EDR or Patch Management Agents.
- Software Vulnerabilities (CVEs): Just like our inventory, we will ingest, aggregate, and deduplicate CVE findings from multiple sources. The unique list of reported CVEs hold their own page within Sevco, and can be prioritized for remediation individually (within this page), or holistically with other types of vulnerabilities.
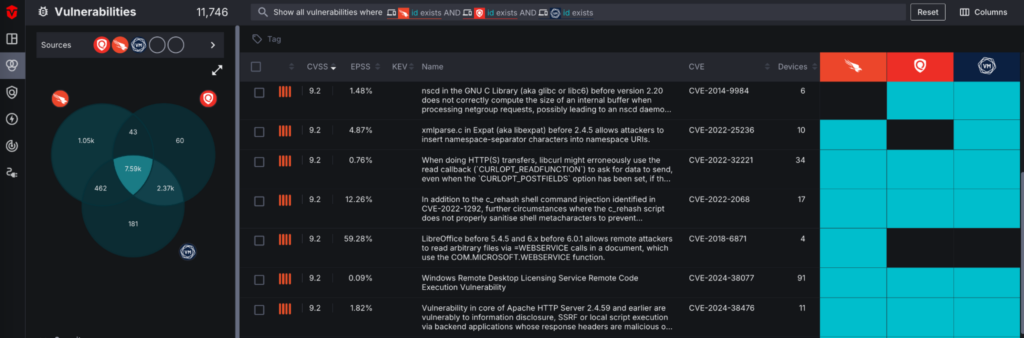
- CSPM (Cloud Security Posture Management) and ASPM (Application Security Posture Management) Vulnerabilities: As modern enterprises continue to migrate to the cloud, and the number of born in the cloud companies grow, so does the requirement for CSPM and ASPM vulnerability management. Like our CAASM and CVE vulnerabilities, CSPM and ASPM vulnerabilities are ingested from specific CSPM / ASPM vendors, and hold their own space within Sevco. Teams can identify, prioritize, and take action on misconfigurations, insecure APIs, access management issues, etc.
Prioritization of Vulnerabilities
An essential capability of a robust Exposure Assessment Platform is vulnerability prioritization. This isn’t just using the technical severity to rank CVEs. We believe that prioritization is specific to each customer. While tools like CVSS are helpful in managing CVEs, many customers need additional layers of context to effectively prioritize. Sevco goes beyond simplistic severity scores to provide nuanced, context-aware prioritization:
- Severity: a measure of how much a security vulnerability could impact a system or application. Sevco leverages industry standard frameworks to support prioritization based on vulnerability severity (e.g. CVSS, CISA Kev, EPSS).
- Exploit Likelihood: the probability that a discovered vulnerability will be actively exploited by a malicious actor. Sevco’s native exploit intelligence incorporates real-world data on exploits observed in the wild (e.g. exploit maturity, threat actor information, and patch availability). Learn more about exploit intelligence in Sevco’s platform.
- Business Context: Bespoke business information needs to be considered in prioritization. Sevco’s deep intelligence of all assets (specifically devices and users) create custom levels of prioritization – think asset criticality, asset ownership, etc.
- Normalized Risk Quantification: Sevco normalizes risk scoring across the different types of vulnerabilities (CAASM, CVE, CSPM, and ASPM), enabling holistic prioritization of critical risk across the attack surface. Gone are the days of siloed prioritization.
Learn the power and flexibility of vulnerability prioritization with Sevco here:
Validation of Exploitability
Layering the internal context and relevant external information is critical to having the right prioritization. Sevco’s intelligence enables customers to validate if an exposure or vulnerability has a proper chance of exploitation, ensuring that prioritized exposures represent true risks. Key capabilities include:
- Control Validation: Verifies the presence and state of mitigating security controls that could prevent exploits.
- Threat Intelligence: Intelligence on the tactics, techniques, and procedures bad actors are leveraging to execute malicious activities. And, leveraging the intelligence to determine if assets are vulnerable to the TTPs.
- External Visibility: Shows whether assets are external-facing and can be reached via the internet by bad actors.
Remediation (CTEM Mobilization)
Remediation is not solely the responsibility of the Security team – it is an organization-wide effort that requires orchestration between Security, IT, and the business. Sevco helps align and mobilize these teams by providing the data they can use to address exposures and proactively harden the security posture of the organization:
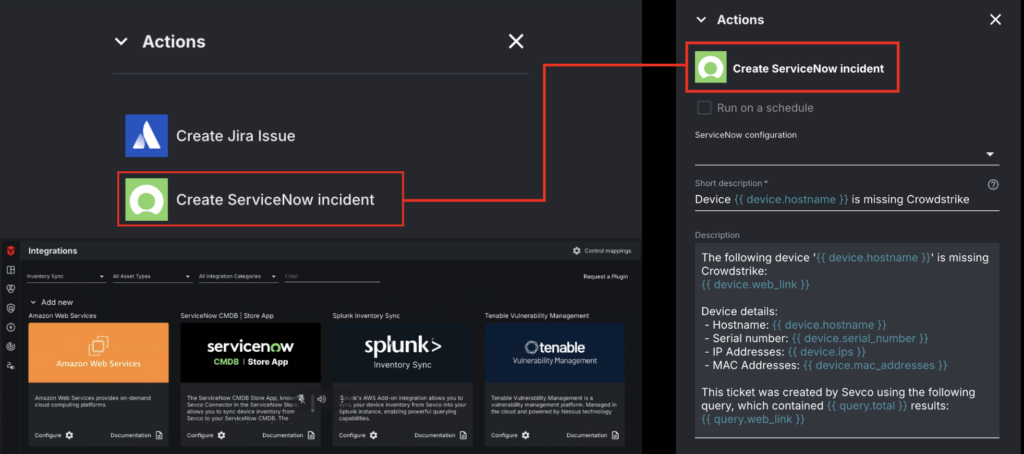
- Action Center: Taking Sevco data to kick off remediation efforts. Action Center automates workflows through bidirectional integrations with ITSM, CMDB, and SIEM tools. Whether it’s notifications in email or slack, ticket creation, or data enrichment, Sevco can facilitate the remediation process. And, our live security inventory can automatically verify when risk has been resolved. A complete feedback loop.
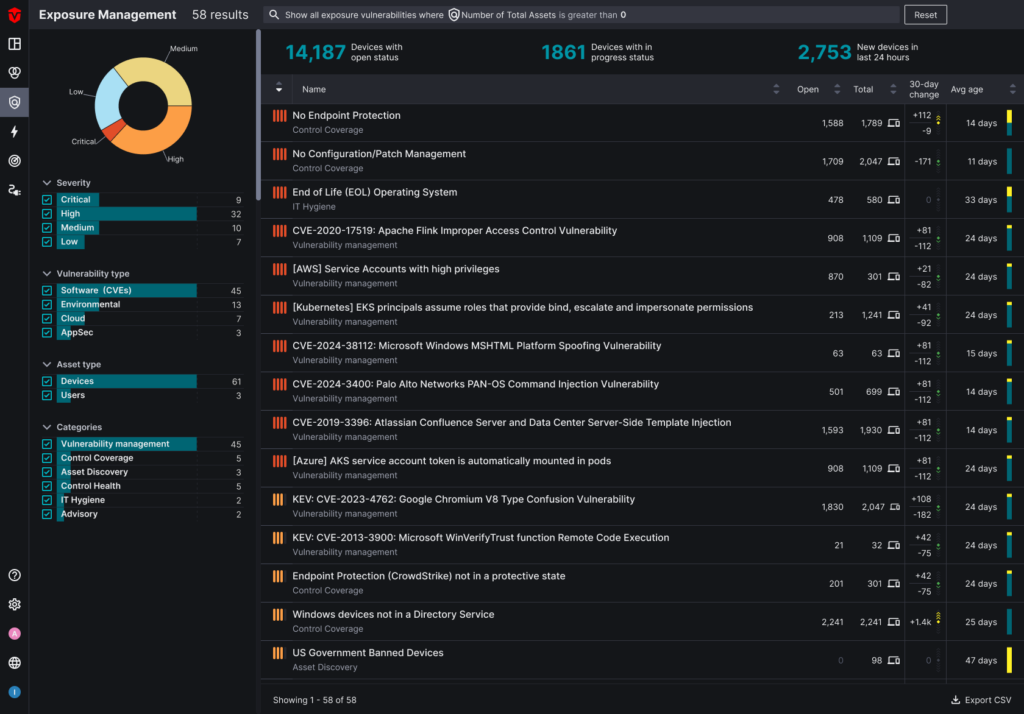
- Exposure Management: After normalizing risk across different classes of vulnerabilities (CAASM, CVE, CSPM, ASPM), we prioritize the critical vulnerabilities in a single-pane of glass called Exposure Management. The page is both a way to review the biggest concerns to the organization, but also to monitor their resolution, and report on key health metrics related to vulnerability and patch management.
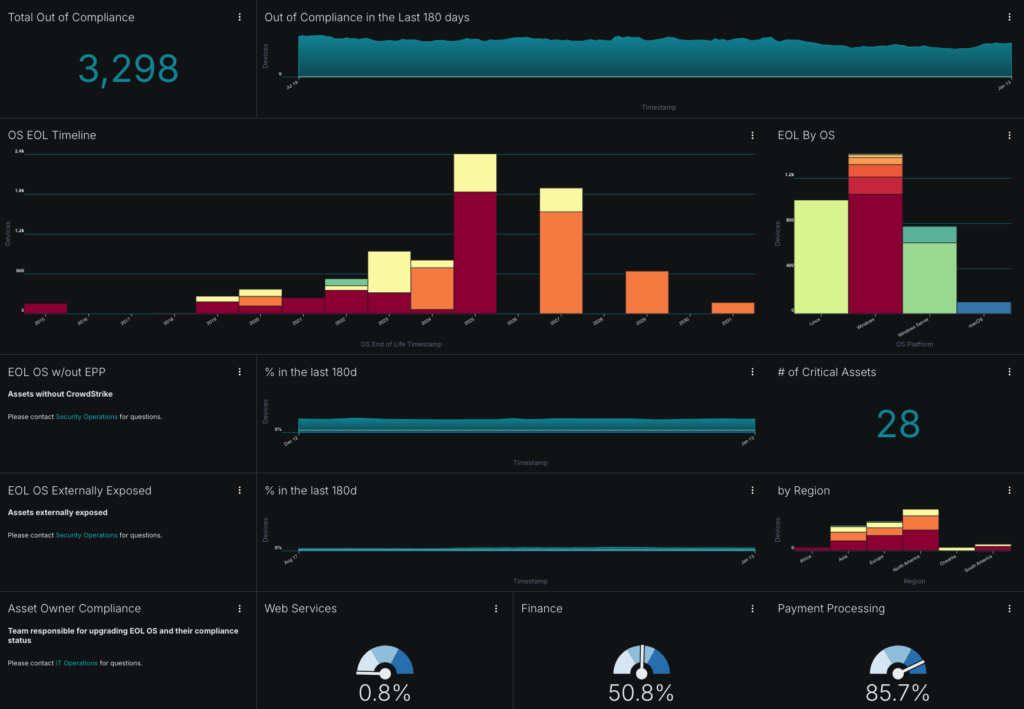
- Custom Reporting: Like our philosophy on prioritization, we believe that reporting often requires customization per customer. As such, we’ve developed flexible dashboards and reports that allow for tracking of bespoke initiatives.
Sevco Can Help
Bad data leads to bad decisions. A single missing asset or vulnerability can compromise the entire risk assessment. Siloed and inconsistent datasets lead to inefficient and ineffective risk management.
By centralizing the assets and intelligence teams require to find, prioritize, and remediate vulnerabilities, Sevco’s Exposure Assessment Platform becomes mission control for security teams, addressing these challenges head-on by empowering organizations to:
- Gain full visibility into assets and associated vulnerabilities
- Prioritize and validate risks based on context
- Mobilize remediation efforts effectively and collaboratively
See Sevco in Action: Request a demo today to see how Sevco can transform your approach to exposure management.
How Sevco Evolved From Assets to Exposures
You Don’t Know What You Got (Why Sevco Was Founded)
Sevco’s co-founders came from the world of EDR – they were on the founding teams of Cylance and Carbon Black. But as they deployed those products, they found one persistent issue with their customers: nobody knew what assets they had. They started Sevco to address the persistent challenges in asset inventory and visibility (CAASM).
Sevco provided a comprehensive inventory of devices, users, software, and controls that made up the attack surface by integrating with existing tools in customer environments. This is a difficult challenge: accurately deduplicating and correlating these assets from multiple tools requires a sophisticated data model that can make inferences to accurately generate a unique inventory.
You Don’t Know Where You’re Vulnerable (Expansion into Vulnerability Management)
Once Sevco provided the complete picture of assets in customer environments, we also surfaced issues like missing or misconfigured agents, end-of-life systems, shadow IT, and other exposures. So in the spring of 2024, Sevco worked to centralize all exposures in one platform, from security gaps to CVEs, by adding vulnerability management capabilities to the original CAASM product.
You Don’t Know What to Do First (Evolution to an EAP)
Sevco didn’t stop there. Organizations have too many issues to address, and too little intelligence on which exposures and vulnerabilities present the greatest risk. Fortunately, Sevco’s data model brings the comprehensive intelligence needed to more effectively prioritize vulnerabilities for remediation. We built flexible, powerful prioritization capabilities into the platform, and uniquely centralized the greatest risks of all types – CVEs, missing agents, business-critical assets missing security controls – into a single dashboard, prioritized by risk. Today, Sevco offers a complete Exposure Assessment Platform, empowering organizations to operationalize their CTEM programs effectively.
Other tools trying to address this were first built with different capabilities – say, vulnerability scanning, or EDR – and have backed into exposure management through acquisitions or new functionality without effectively investing in the foundation required for an effective CTEM program: comprehensive visibility of the assets that make up the attack surface. In these tools, blindspots and duplicates persist.
Sevco, however, was built from the ground up to provide inventory, vulnerabilities, exposures, threat intelligence, and mobilization through remediation from a single platform.
