Continuous Threat Exposure Management:
The Foundation of Modern Cybersecurity
The Foundation of Modern Cybersecurity
Introduction: The Need for Continuous Threat Exposure Management (CTEM)
With the increasing complexity of IT environments, organizations face challenges in addressing the vast array of cyber exposures that leave them vulnerable across the attack surface. Traditionally, security teams have largely focused on prioritizing and remediating software vulnerabilities, CVEs. But, as the breadth of threats to IT environments has expanded beyond CVEs to include security gaps such as missing security tools and agents, misconfigurations, end-of-life systems, shadow IT, vulnerable cloud, code, and more—security teams need a more robust program to address all of these exposures. Vulnerability management programs, while valuable, are too limited in scope and must evolve to address the broader landscape of threats.
Continuous Threat Exposure Management (CTEM) programs have emerged as a revolutionary approach to addressing these gaps, enabling organizations to manage vulnerabilities and risks holistically and continuously. Here, we explore the principles, process, and benefits of CTEM programs, providing a framework teams can leverage to implement their own programs and underline some of the pitfalls organizations might run into as they begin to operationalize these practices.
CTEM programs require the union across many categories of solutions to be successful. Best-in-class programs implement what Gartner is calling Exposure Assessment Platforms – EAP for short, we do love our acronyms – which consolidate many of these capabilities into one platform, either through integrations with existing tools or through native capabilities, to provide a single pane of glass through which security teams can manage, mobilize, and measure the success of their CTEM programs. We’ll describe these tools in greater detail below.
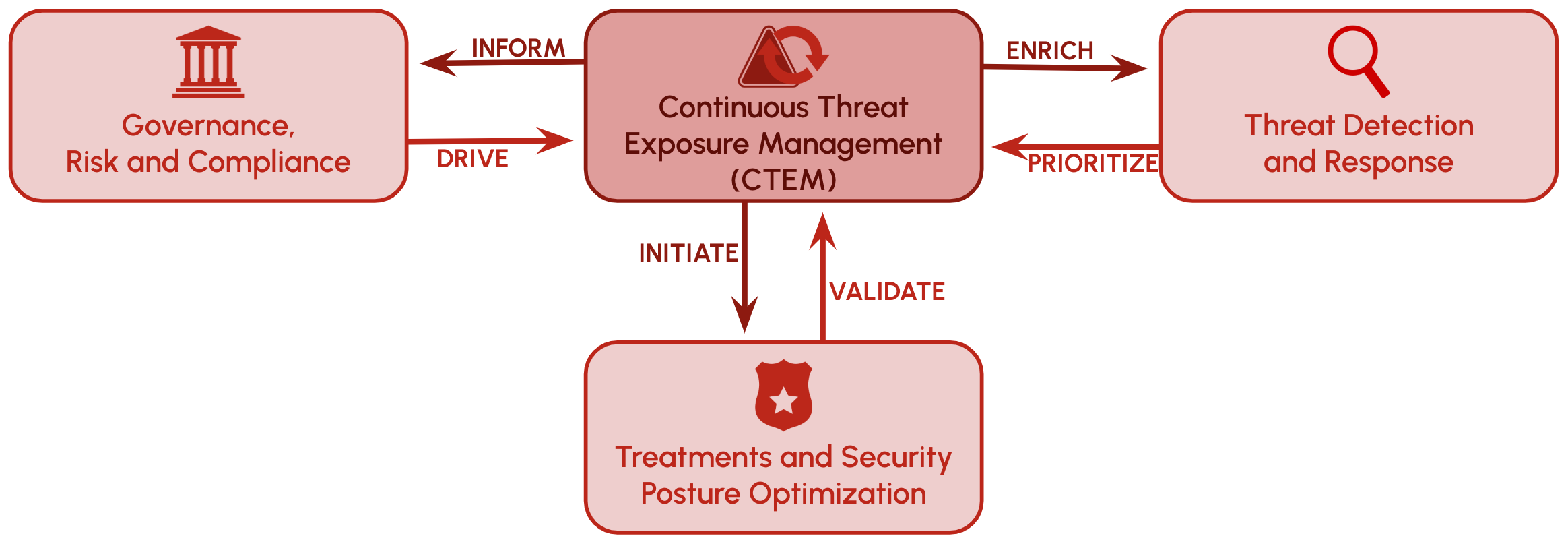
How Does CTEM Compare to Other Approaches?
CTEM is the process of identifying, assessing, prioritizing, validating, and remediating cyber exposures across an organization’s attack surface. There are alternative approaches, but these have some notable differences and shortcomings:
- Vulnerability Management/RBVM: focuses on reducing risk by uncovering software vulnerabilities through scans or agents on assets, then using static analysis to prioritize and remediate them. The number of assets analyzed can be large, and the number of vulnerabilities discovered continues to grow, so vulnerability management requires automation to be effective. However, vulnerability management tends to be limited to finding and remediation CVEs, so it doesn’t address the broader set of exposures like misconfigurations, shadow IT, end-of-life systems, security gaps, and more. Further, prioritization tends to be limited to technical severity, so many organizations have a growing backlog of vulnerabilities they need to address and limited understanding of the risks vulnerable assets pose outside of the criticality of the vulnerability.
- Red Team exercises: these are expensive, single-instance, manual tests of exposures and cyber defenses meant to prevent attackers from breaching environments. They aim to identify whether an attacker can leverage an exposure to successfully attack an organization at a point in time, but are limited in identifying a broader range of risks.
- Penetration Testing: similar to Red Team exercises, penetration testing uses a testing methodology to assess risks in the environment, and provides a view of those risks at the time the testing was conducted. Penetration testing can risk outages, so critical assets are not always tested to prevent this.
- Cloud Security Posture Management (CSPM): provides visibility into misconfigurations and compliance risks in cloud environments. As the name suggests, this ignores remote employees, on-premise assets, and can overlook interactions between multiple cloud vendors in some environments. These solutions may not be able to expose the full path of attacks that cross between environments which can happen in the real world.
CTEM addresses the limitations of these approaches to be more inclusive, comprehensive, continuous, and realistic:
- All assets: effective CTEM programs will address cloud, on-prem, and remote assets and leverage context tailored to each organization to understand which ones are the most critical.
- Continuous and comprehensive: as the name suggests, CTEM programs continuously discover all types of exposures, from traditional vulnerabilities like CVEs to misconfigurations, security tool coverage gaps, end-of-life systems, and more.
- Flexible prioritization: effective CTEM programs will leverage multiple layers of prioritization, from technical severity to asset criticality and exploitability, to assess which exposures on which assets pose the greatest risks. Prioritizing remediation efforts to eliminate those paths with the fewest fixes.
- Effective remediation: beyond prioritizing the greatest risks, CTEM programs should identify the most effective remediation actions to take to address the most risks. For example, rolling out a single patch that incorporates fixes to multiple severe CVEs on each asset vs. a single critical CVE.
Ultimately, an CTEM program is continuously monitoring your environment for exposures (that’s why it’s Continuous Threat Exposure Management), assessing the risks they pose both from the perspective of their exploitability and the unique risk they pose to your environment based on the business context of the affected assets (like the business processes they support, the users who interact with them, or the data contained within them), and ensuring fast, effective remediation of the riskiest exposures.
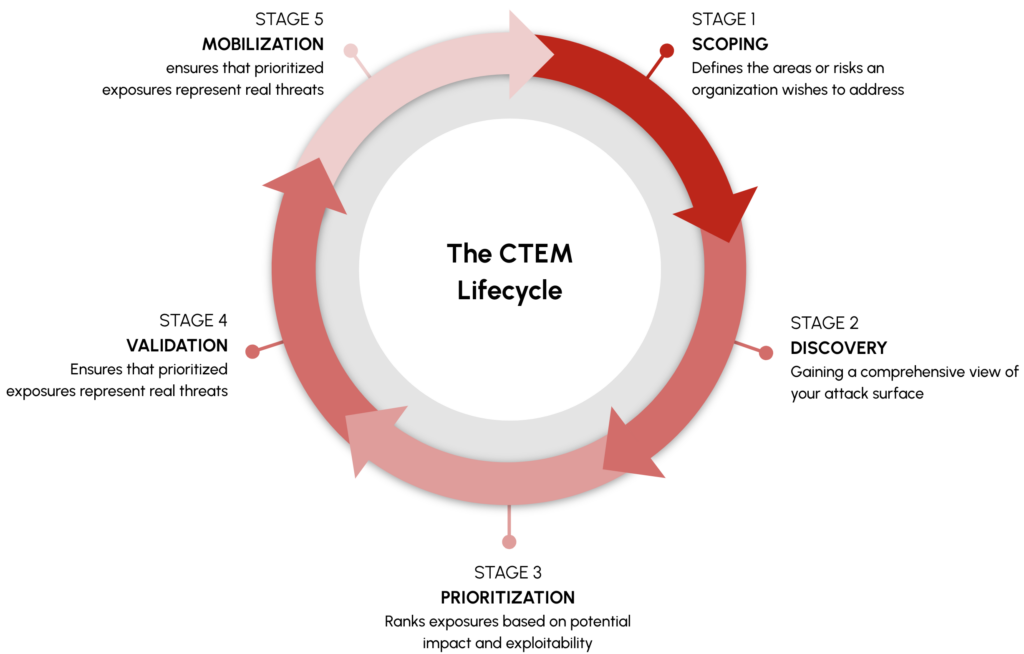
The CTEM Lifecycle
There are five distinct phases that a successful CTEM program will implement to achieve these benefits.
1. Scoping
Scoping defines the areas or risks an organization wishes to address. This phase aligns the CTEM process with business priorities and risk profiles. Tools that support this phase include:
- Attack Surface Management (ASM): Identifies and maps an organization’s external and internal attack surface.
- External Attack Surface Management (EASM): Focuses on public-facing assets vulnerable to external threats.
- Cyber Asset Attack Surface Management (CAASM): Provides unified visibility into all cyber assets to inform the scope of assessment.
- Supplementary Tools: SaaS Security Posture Management (SSPM) and Digital Risk Protection (DRP) enhance scoping by identifying risks specific to cloud and digital assets.
2. Discovery
Discovery is foundational to gaining a comprehensive view of your assets, any vulnerabilities, control deployment and synthesizes this data into an overview of the exposures in your environment beyond just CVEs. Modern Exposure Assessment Platforms (EAPs) aggregate data from multiple sources, providing a holistic view of vulnerabilities.
A well-executed discovery phase will:
- Provide a comprehensive inventory of your devices, identities, software, cloud assets, applications, and the deployment of your controls.
- Scan this now complete picture of your assets for CVEs with Vulnerability Assessment tools
- Consolidate intelligence from all of the tools in your tech stack into a single pane of glass, driving more efficient and effective decision-making because insights are no longer siloed in different tools
- Map the relationships between your devices, vulnerabilities, and users, adding critical business context to each exposure and see interconnected risks
3. Prioritization
Prioritization ranks vulnerabilities based on their potential impact and exploitability, providing normalized, context-aware prioritization to uncover the highest-impact security risks so security teams know exactly where to focus their efforts at remediation first. Core factors include:
- Severity: The impact on confidentiality, integrity, and availability.
- Threat Levels: Known exploits and active exploitation trends.
- Exploitability: Ease of exploitation in the current environment.
- Business Impact: Financial and operational consequences of exposure.
A comprehensive asset inventory is fundamental to this phase. Sevco’s platform, for example, integrates detailed visibility into every asset on the network, including:
- Presence: Accurate inventory of devices, users, software, vulnerabilities, and controls.
- State: Real-time data on asset attributes, including the health of tools and their protective capabilities.
- Business Context: Intelligence on asset criticality, user access, and operational importance.
- Mitigating Controls: Visibility into the deployment of your security controls which might mitigate the risks of certain exposures.
A holistic view ensures that prioritization considers not just technical severity but also the unique business impact to your organization that the breach of an exposure would have. Security teams have limited bandwidth, so this step ensures your security teams are focusing on high-value and high-risk exposures. Indeed, you can write an entire white paper on just this step of the exposure management lifecycle (which we did – we’ve created this deep dive into the many facets of vulnerability prioritization).
4. Validation
Validation ensures that prioritized exposures represent real threats. By running realistic attack simulations, this phase confirms which vulnerabilities could be exploited in a real-world scenario. Supporting technologies include:
- Attack Path Mapping: The identification and analysis of potential paths an attacker could take to infiltrate a system or network.
- Breach and Attack Simulation (BAS): Tests the effectiveness of security measures against simulated attacks.
- Automated Pentesting and Red Teaming: Identifies exploitable vulnerabilities through automated adversarial techniques.
Validation reduces operational burden by filtering out theoretical risks, allowing security teams to focus on actionable threats.
At Sevco, we often talk about another kind of validation – remediation validation – which we’ll touch on in the next step.
5. Mobilization
Mobilization routes validated exposures to the appropriate remediation teams. Key steps include:
- Assigning tasks based on criticality scores.
- Automating workflows using ticketing systems and dashboards.
- Providing ready-to-deploy mitigation strategies to simplify remediation efforts.
Tools like Sevco’s platform enhance mobilization by integrating with ticketing tools and automating the creation of tickets to remediate exposures, and then validate when the remediation is effective – not when tickets are closed, but when patches are deployed, misconfigured EDR agents are fixed, or end-of-life systems are deprecated and no longer observed. This ensures that remediation efforts are effective, efficient, and actually reducing risks across the environment.
Best Practices for CTEM
Implementing an effective CTEM program requires adherence to proven best practices:
- Maintain a Comprehensive Asset Inventory: Ensure accurate and up-to-date records of all assets, including their locations, configurations, and criticality to business operations. This is the foundation of any effective CTEM program.
- Integrate CTEM into Existing Security Workflows: Embed exposure assessment and prioritization into daily security operations to create a seamless and proactive approach to threat management.
- Validate Threats with Real-World Simulations: Use adversarial techniques such as breach and attack simulations to confirm that identified vulnerabilities are exploitable. This ensures resources are directed toward real risks.
- Prioritize Based on Business Impact: Align remediation efforts with organizational goals by focusing on vulnerabilities that pose the highest risk to critical assets and business functions.
- Automate Where Possible: Leverage automation for tasks like asset discovery, vulnerability scanning, and ticket generation to increase efficiency and reduce manual effort.
- Foster Collaboration Across Teams: Involve stakeholders from IT, security, and business units to ensure alignment on priorities and effective implementation of remediation strategies.
- Continuously Update and Evolve: Treat CTEM as an ongoing process that adapts to the evolving threat landscape, ensuring defenses remain effective against new vulnerabilities and attack methods.
Where CTEM Programs Can Fail
While exposure eanagement offers a comprehensive approach to managing cyber risks, organizations may encounter challenges that hinder its effectiveness. We highlight a few of these risks here so that organizations can understand what roadblocks they might encounter, and can strategize ways to mitigate these:
- Incomplete Asset Inventory: Without an accurate and up-to-date inventory of all devices, users, software, and vulnerabilities, prioritization and remediation efforts can miss critical gaps.
- Lack of Validation: Skipping the validation phase may lead to wasted resources on theoretical risks while overlooking real, actionable threats.
- Poor Integration of Tools: Disconnected tools and platforms can create silos, reducing the visibility and efficiency of the CTEM program.
- Inadequate Stakeholder Buy-In: Without support from key stakeholders, such as executive leadership and IT teams, CTEM initiatives may struggle to align with business priorities and secure the necessary resources.
- Overwhelming Data Volume: Failing to leverage automation and advanced analytics to process large volumes of exposure data can overwhelm security teams and slow down response times.
- Unclear Remediation Protocols: Without well-defined processes for mobilization, teams may face delays in addressing validated exposures, leaving vulnerabilities unaddressed.
By addressing these potential pitfalls, organizations can maximize the effectiveness of their Continuous Threat Exposure Management programs and build a more resilient security posture.
Conclusion
Continuous Threat Exposure Management represents the future of cybersecurity, providing a comprehensive, continuous approach to managing vulnerabilities and risks. By following the structured lifecycle of scoping, discovery, prioritization, validation, and mobilization, organizations can build a resilient security posture. A robust asset inventory underpins the entire process, ensuring visibility and efficiency in managing the ever-evolving threat landscape.
Request a demo today to see how Sevco can transform your approach to exposure management.
