The New Approach to Comprehensive Vulnerability Management
The Vulnerability Prioritization Problem
Over the past 20+ years, vulnerability management has evolved from a simple, primarily manual process to a complex multistage process. Responsibilities are spread across multiple teams and some automation has been implemented to improve vulnerability prioritization. But growing backlogs of critical vulnerabilities underscore how there’s still work to be done.
Effective vulnerability management requires comprehensive vulnerability and threat data. A complete inventory of devices, identities, software, and controls is also critical to prioritize vulnerabilities as risks to your environment. And while most vulnerability prioritization processes are focused on software vulnerabilities like CVEs, the most mature vulnerability management programs address vulnerabilities like missing or misconfigured agents, end-of-life systems, cloud misconfigurations, shadow IT, and more.
While we’re primarily focused on providing more effective ways for vulnerability prioritization, it’s important to review how vulnerability management programs have evolved. To address the backlog and threat of vulnerabilities in increasingly complex IT environments, organizations have had to reassess their vulnerability management programs.
The early problem: Vulnerability identification
Prior to 1998 and the introduction of Nessus, the free remote security scanner, there were a few tools used to identify vulnerabilities. However, most vulnerability assessments, even with the introduction of Nessus (and for almost a decade later), were local to the system.
The next big problem: Vulnerability classification
In 1999, the MITRE Corporation launched CVE (Common Vulnerabilities and Exposures) to identify and categorize vulnerabilities in software and firmware.
Identification and classification
With the introduction of scanning tools and CVE, it became possible to continuously assess for vulnerabilities—in a limited scope.
Proliferation of vulnerability assessment brought additional problems
As tech stacks and sources of vulns have grown, the “Which of these do I fix?” problem has become a larger, more complex problem. The hay stack has grown and teams are overwhelmed.
But that’s not the ONLY problem. And that’s why organizations need a new approach
to address the vulnerability prioritization problem altogether.
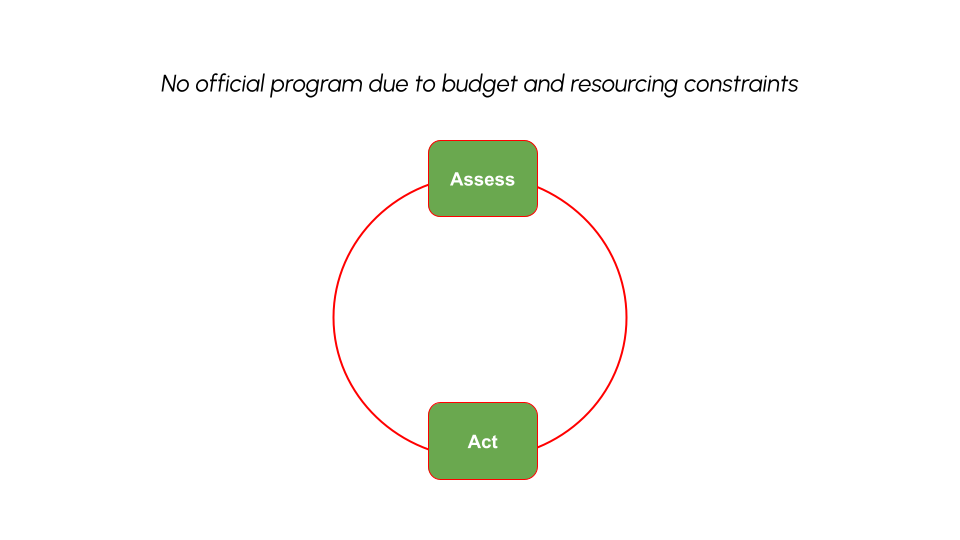
Vulnerability Management: An Immature Program
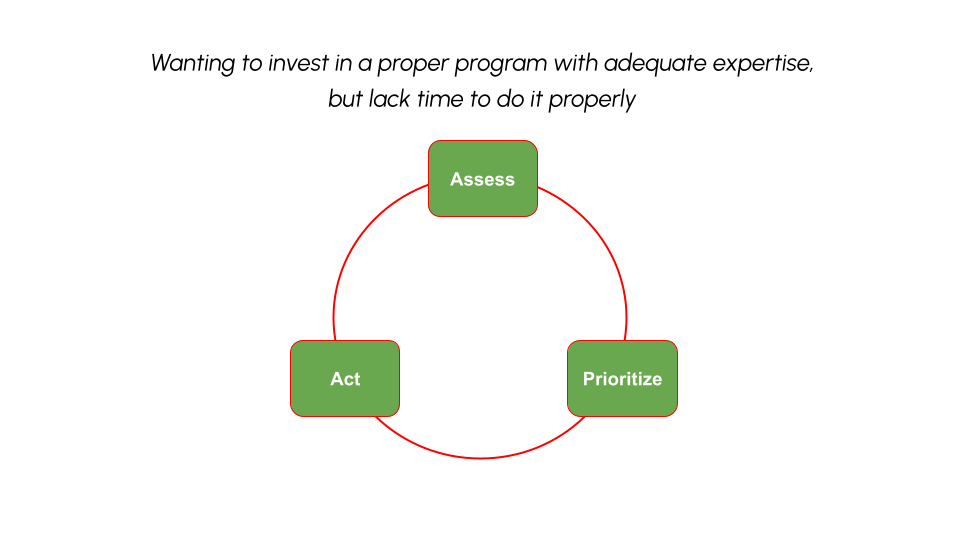
Vulnerability Management: A Maturing Program
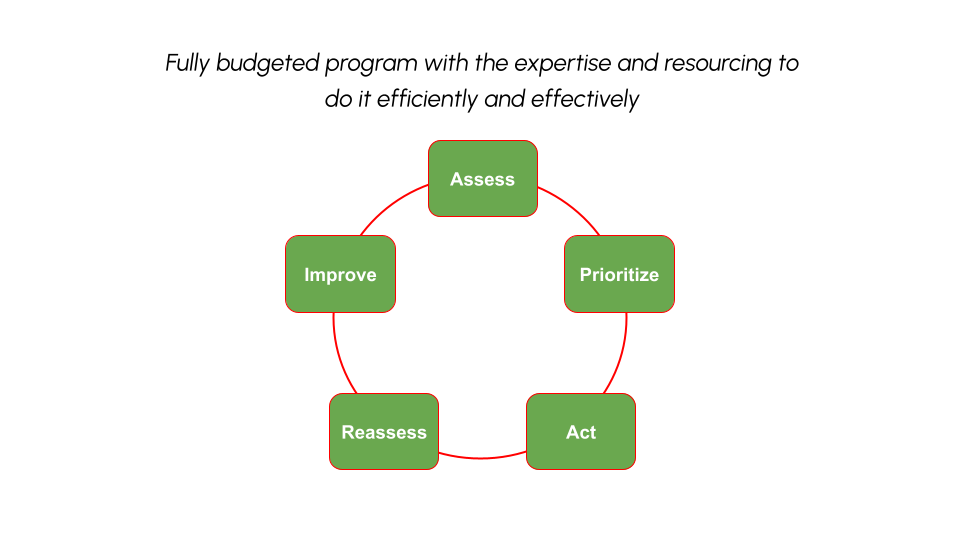
Vulnerability Management: A Mature Program
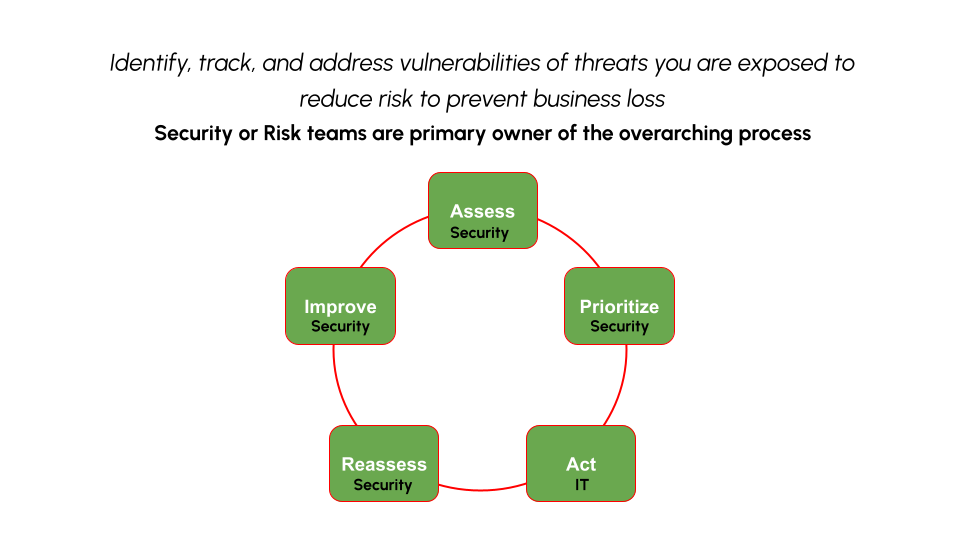
Vulnerability Management by Team
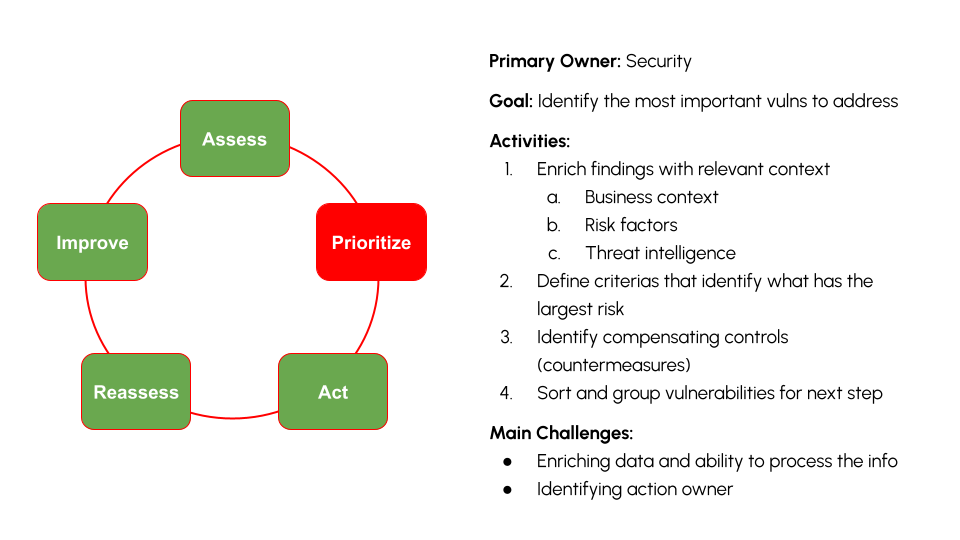
Vulnerability Management: Vulnerability Prioritization