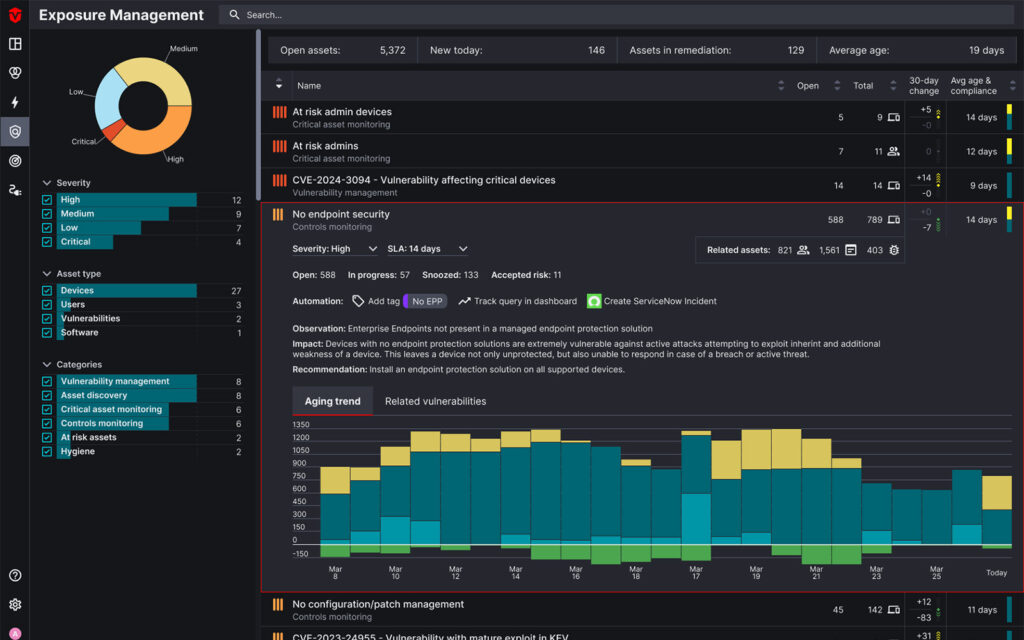
Today, we’re introducing Exposure Management, the next generation of Sevco’s Asset Intelligence Platform. Sevco now supports vulnerability management activities such as aggregation, prioritization, and remediation management. We’ve done the foundational asset inventory work over the past four years and we are now solving one of the biggest challenges in our industry.
Sevco’s Foundational Asset Inventory
We founded Sevco to solve one core problem: managing endpoint agent tool deployments. Our founding team was a bunch of former endpoint guys from Cylance and Carbon Black. Our customers depended on our platforms for their security but they struggled to deploy the agents everywhere. They knew the root cause of this was the lack of a full device inventory – but didn’t know where to get one.
Everyone knew the problem with existing device inventories. There wasn’t a single inventory, but actually dozens in every organization and they all reported different things. Siloed teams, working in siloed tools, each had a different inventory picture. Security teams, accountable for all of it, had no source of truth they could depend on.
The solution was clear. First, aggregate the existing device inventories. Then, accurately associate the duplicate devices reported by multiple sources. Next, give users the tools to analyze endpoint agent deployment. Finally, automate the deployment gap remediation process.
Of course, devices are only one of the major IT asset classes, and not the only one with siloed data and no single source of truth. After solving the device inventory problem, we’ve since expanded the asset classes we support to include identity and software. For each, the process to create the trusted inventory remains the same.
For four years, we have focused on breaking down the data silos. We have created a source of truth for one asset class after another, which enables our customers to improve their security programs.
Vulnerability Aggregation: Vulnerabilities as an Asset Class
Today, we are introducing a fourth asset class supported in the Sevco platform: vulnerabilities.
Fifteen years ago, there was one kind of vulnerability: CVEs. We had one platform reporting CVEs: the vulnerability assessment scanner. Today, we have many systems reporting CVEs and many platforms reporting vulnerabilities in other categories such as cloud, identity, system misconfigurations and more. Further, the volume of vulnerabilities within each category has exploded. We are drowning in vulnerabilities, and identifying the highest risk vulnerabilities has never been harder.
We are tackling those challenges head-on.
Introducing Sevco’s Cross-Class Vulnerability Prioritization
Alongside vulnerability aggregation, we are also introducing vulnerability prioritization. Aggregating vulnerabilities is not enough. We must also help organizations identify the highest-risk vulnerabilities to address: whether they be CVEs or one of the other many classes of vulnerability.
Our vulnerability prioritization is different from existing vulnerability prioritization technologies:
- A comprehensive device inventory is the foundation. It doesn’t matter how many times you open the remediation ticket with IT: if your patch management agent isn’t there, nothing gets patched. If the vulnerability management agent isn’t there, you won’t see it at all. Our research shows these agents are missing on about 20% of your devices.
- We create a comprehensive vulnerability inventory. It doesn’t matter how many different products you have reporting CVEs. We will aggregate them into a single, de-duplicated list.
- We prioritize across vulnerability classes. We prioritize CVEs alongside missing endpoint agents and other IT hygiene vulnerabilities so you can always work on the highest risk issues first.
- We use bleeding-edge technical prioritization. CVE enrichments such as the CISA Known Exploited Vulnerabilities database ensures your team is working on the most important CVEs.
- We have the industry’s best business context prioritization. Based on our industry-leading device inventory, we don’t limit you to a few manually-configured fields to describe business context. You can use any attribute from any inventory to adjust prioritization. If you can imagine it, you can prioritize it.
Remediation Management: Completing the Workflow
A prioritized list of vulnerabilities is just the start. To reduce risk, those vulnerabilities must be remediated. We support the remediation process as well. The key pillars of our remediation management support are:
- We automate remediation. Remediation is a collaboration between security, system owners and system users. Sevco includes integrations with systems used for remediation processes. You can automatically create tickets for the IT Ops team in ServiceNow, while automatically creating tickets for the DevOps team in JIRA.
- We report amazing remediation metrics. Are your remediation procedures working? Which IT teams are meeting the remediation SLA and which ones are not? Which issue types are under control and which ones need attention? We track the efficacy of your remediation procedures so you can manage the process and ensure the many teams involved are operating on the same set of data and operational metrics.
- We validate that remediation actually happened. A closed ticket doesn’t mean the issue was fixed. We see these issues in the wild through your infrastructure. We keep state over time, so we report when an issue was actually fixed, no matter the ticket status.
Management legend Peter Drucker said “You can’t manage what you can’t measure.” But poor vulnerability data has made it hard for security teams to get good metrics for remediating vulnerabilities. Sevco is changing that.
Closing
Sevco is moving the needle on industry – again. We’ve already changed the game with asset inventory. Our customers can manage their endpoint agent deployments in a way that no other technology allows. We’re doing it again with vulnerability management, in ways that are not possible without the asset inventory foundations.
This is not the end of our journey into vulnerability management, but just the beginning. If you’re interested in learning more and helping shape this future, reach out and book a demo today.
