Exposure Management.
Full-cycle vulnerability prioritization, remediation validation and
analytics from a single dashboard.
Vulnerabilities lurk where you lack visibility.
Built on the foundation of the industry’s first complete asset inventory, Sevco’s Asset Intelligence Platform enables the prioritization, automation, and validation of remediation across multiple vulnerability classes including CVEs and environmental vulnerabilities like missing security tools and IT hygiene issues.
Vulnerability Database.
The single source of truth for vulnerabilities in your environment.
Stop relying on vulnerability scanners that may be missing 31% of your assets. Sevco surfaces multiple classes of vulnerabilities—
including CVEs and environmental vulnerabilities like missing security controls and IT hygiene issues—all in one platform.
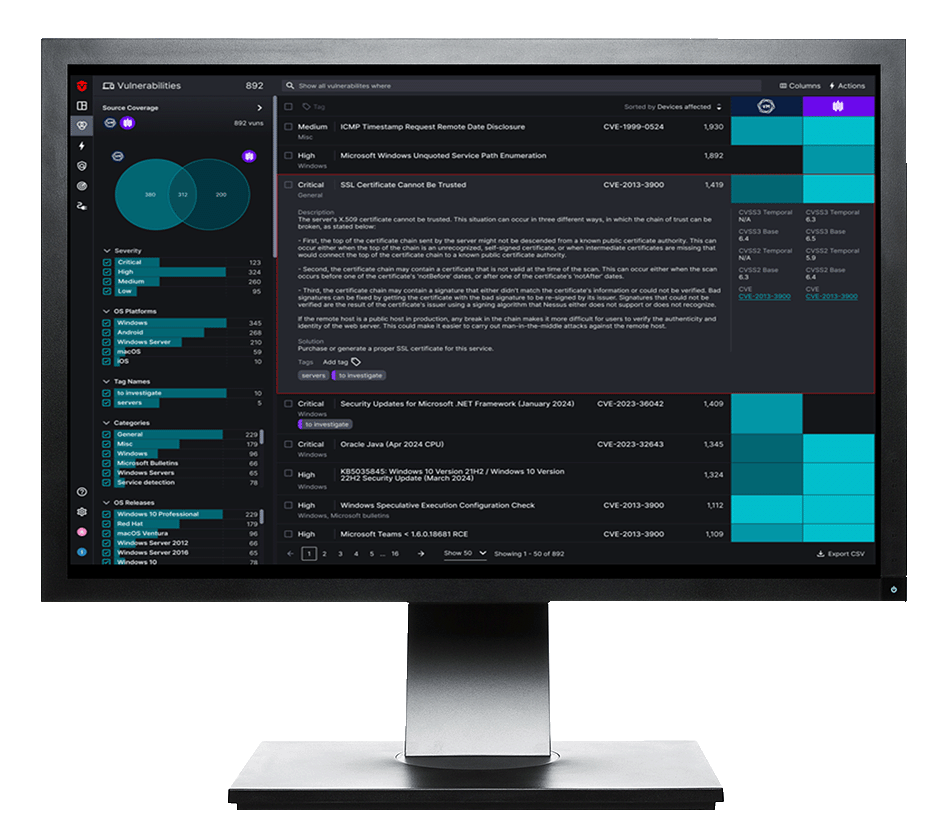
Sevco provides a complete view of exposures by surfacing multiple classes of vulnerabilities including CVEs, missing or misconfigured security controls, or EOL systems and shadow IT.
With a complete software inventory, Sevco can quickly surface CVEs—without having to rely on vulnerability scanners.
By providing extensible asset data, Sevco enables you to add business related context (executive users, system admin access, etc.) so you can better determine and action the risk specific to your organization.
The Vulnerability Database records and tracks when vulnerabilities are discovered, actioned, and if remediation SLAs aren’t met.
Prioritization Engine.
Comprehensive visibility enables comprehensive prioritization.
Prioritize risk based on your environment.
By providing a comprehensive view of all devices, users, software, tools, and vulnerabilities—and the relationships between them—
Sevco enables you to confidently assess risk to determine the most impactful actions.
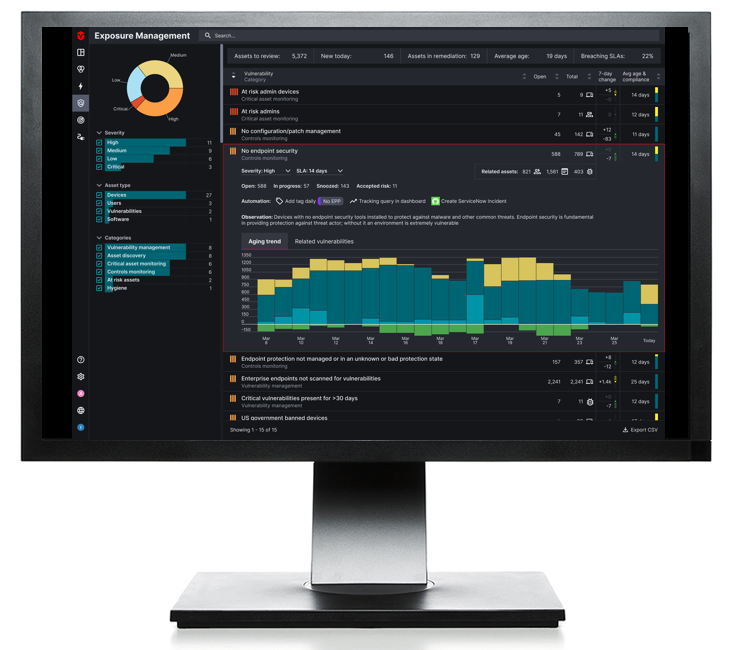
Sevco surfaces all classes of risk exposures in your environment, including CVEs, assets missing security controls, or IT hygiene issues.
Prioritize risk not only on technical severity but on business impact. Configure queries based on complex criteria including users, asset type, software version, and state. If you can describe it from the query, you can use it as a condition to prioritize.
With comprehensive correlation of assets and vulnerability classes, you’ll have the visibility and data to determine if it would be more effective to patch 5 devices with CVEs or deploy EDR to 50 devices—including the 5 with CVEs.
Customize SLAs based on vulnerability and business impact. Track remediation of exposures against SLAs with remediation validation and analytics.
Based on the comprehensive context provided by Sevco, you can snooze risks for future action or accept the risks and review the known vulnerabilities at a later time.
Innovative technology behind comprehensive asset intelligence.
Platform Overview
The high-level view of how Sevco’s platform provides asset intelligence and vulnerability prioritization.
Security Asset Inventory
The foundation of every security program is an accurate and real-time asset inventory.
Remediation and Validation
Automated remediation and remediation validation at the asset level.
Analytics and Reporting
Track and monitor effectiveness of remediation, net changes impacted assets, MTTR, and more.
What our customers say about us
The latest in asset intelligence.

Take your vulnerability managment to the next level
Reduce risk exposure by prioritizing and remediating CVEs and environmental vulnerabilities like missing agents. Confirm remediation efficacy to improve security processes and reduce exposure.
AWARDS
Proud to earn industry trust.













